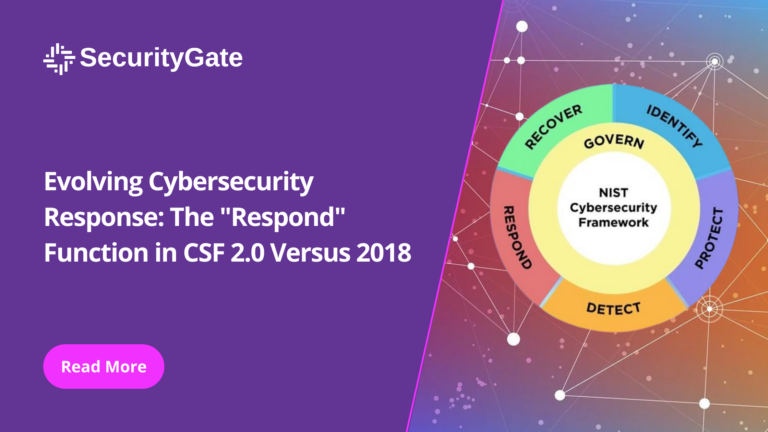
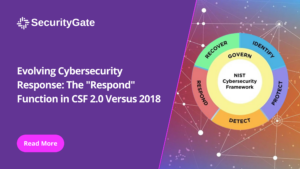
The capacity to respond effectively in a cybersecurity incident is critical for minimizing impact and restoring operations. The “Respond” function of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) equips organizations with the principles needed for an efficient and effective response.
With the introduction of CSF 2.0, significant updates have been made to this function, reflecting advancements in response to strategies and technologies. This blog post examines these changes, highlighting the evolution from the 2018 framework to CSF 2.0 and what it means for organizations striving to bolster their cybersecurity defenses.
The Core of the “Respond” Function
The “Respond” function encompasses an organization’s actions once a cybersecurity event is detected. It’s about having the right plans, processes, and communication strategies in place to mitigate an incident’s effects swiftly and efficiently.
Notable Changes in CSF 2.0
- Incident Management
While the 2018 CSF included aspects of incident response, CSF 2.0 places a renewed emphasis on “Incident Management” as a category. This enhancement reflects a broader approach to managing incidents, not just from a technical standpoint but also considering the organizational, legal, and communication aspects. It stresses the importance of comprehensive incident management policies and procedures that are well-integrated within the organization’s cybersecurity strategy.
- Incident Analysis
CSF 2.0 introduces “Incident Analysis” as a critical component of the “Respond” function. This addition underlines the necessity of a detailed examination of incidents to understand their cause, scope, and impact. Incident analysis is crucial for learning from events, improving security measures, and preventing future occurrences. This analytical approach signifies a shift towards more proactive and informed response mechanisms.
- Incident Response Reporting and Communication
Enhanced focus on “Incident Response Reporting and Communication” in CSF 2.0 demonstrates the growing recognition of the importance of communication before, during, and after an incident. Effective communication with internal and external stakeholders, including regulatory bodies, customers, and the public, is crucial for maintaining trust and managing the reputation impact of cybersecurity events.
- Incident Mitigation
“Incident Mitigation” remains a vital category within the “Respond” function, with CSF 2.0 emphasizing deploying strategies and actions to limit the impact of cybersecurity incidents. The updated framework encourages organizations to be more agile and effective in their mitigation efforts, utilizing established protocols and innovative solutions to address threats dynamically.
Implications for Organizations
- The refinements in the “Respond” function within CSF 2.0 highlight the evolving nature of cybersecurity incident response. Organizations are encouraged to:
- Enhance Incident Management Practices: Develop and regularly update incident management policies that encompass all aspects of an organization’s response to cybersecurity events.
- Foster Analytical Capabilities: Invest in training and tools to support in-depth incident analysis, enabling a better understanding of threats and informing future security improvements.
- Strengthen Communication Protocols: Establish clear communication channels and protocols for incident reporting, ensuring that all relevant stakeholders are informed and engaged appropriately.
- Prioritize Incident Mitigation: Continuously review and adapt incident mitigation strategies to address the changing threat landscape and leverage the latest technologies and methodologies.
Conclusion
The “Respond” function updates in CSF 2.0 offer a comprehensive framework for addressing cybersecurity incidents, emphasizing management, analysis, communication, and mitigation. By adopting these enhanced practices, organizations can more effectively manage the immediate effects of incidents and build resilience against future threats.
In the constantly shifting cybersecurity domain, staying abreast of these developments, and integrating them into response strategies is essential for safeguarding digital assets and maintaining operational continuity.
Stay tuned for the final blog post in this series next week on the “Recover” Function.