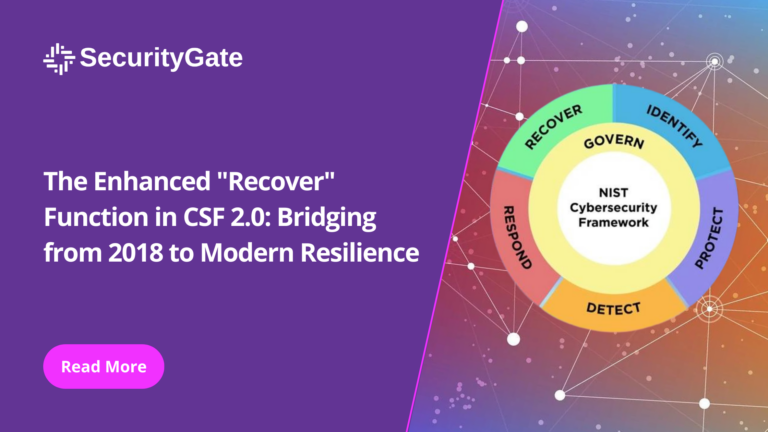
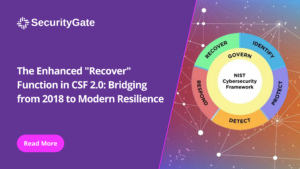
In the aftermath of a cybersecurity incident, an organization’s ability to recover and return to normal operations is crucial for its resilience and continuity. The “Recover” function in the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) is designed to guide organizations through this critical phase.
With the introduction of CSF 2.0, significant enhancements have been made to the “Recover” function, reflecting the evolving landscape of cybersecurity and the increasing complexity of threats. This blog post examines the evolution of the “Recover” function from the 2018 framework to CSF 2.0, highlighting the fundamental changes and their implications for organizations.
Understanding the “Recover” Function
The “Recover” function aims to restore services and capabilities affected by a cybersecurity incident. It involves planning and implementing recovery processes to minimize downtime and mitigate the impact on business operations.
Critical Updates in CSF 2.0
- Incident Recovery Plan Execution
CSF 2.0 places a renewed emphasis on “Incident Recovery Plan Execution.” While recovery planning was always a part of the framework, the updated version underscores the importance of not just having a plan but effectively executing it. This shift highlights the need for dynamic and flexible recovery plans that can be adapted to the specifics of an incident, ensuring that organizations can quickly mobilize their recovery efforts in the face of diverse threats.
- Incident Recovery Communication
Another significant enhancement in CSF 2.0 is the focus on “Incident Recovery Communication.” Effective communication during the recovery process is vital for managing stakeholder expectations, maintaining trust, and ensuring a coordinated recovery effort. This includes clear and timely communication with internal stakeholders, customers, partners, and, if necessary, the public and regulatory bodies. The updated framework recognizes the role of communication in managing the technical aspects of recovery and addressing the reputational and relational impacts of an incident.
Implications for Organizations
The “Recover” function enhancements in CSF 2.0 reflect a comprehensive approach to cybersecurity resilience, emphasizing the need for preparedness, flexibility, and communication. Organizations looking to align with these updated guidelines should consider the following actions:
– Refine Recovery Plans: Ensure that incident recovery plans are in place, regularly updated, tested, and capable of being executed efficiently. This may involve simulations or drills to prepare teams for real-life scenarios.
– Enhance Communication Strategies: Develop robust communication protocols outlining how and when to communicate with all relevant stakeholders during recovery. Communication should include predefined messages and channels to ensure consistency and clarity.
Conclusion
The “Recover” function in CSF 2.0 offers an evolved framework for addressing the challenges of recovering from cybersecurity incidents. By emphasizing plan execution and communication, the updated guidelines encourage organizations to adopt a more thorough and transparent recovery process. Adapting to these changes is essential for organizations aiming to minimize the impact of cybersecurity events and ensure a swift return to normal operations. In the rapidly changing digital landscape, the ability to recover effectively is not just a component of cybersecurity strategy—it’s a cornerstone of operational resilience and long-term success.