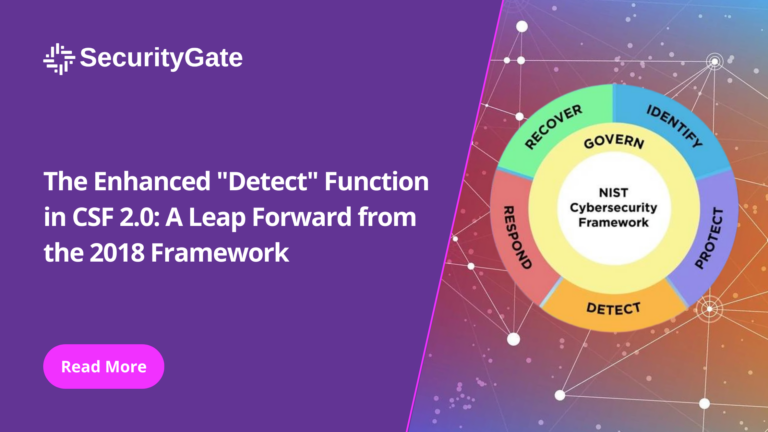
In the evolving field of cybersecurity, the ability to quickly detect anomalies and cybersecurity events is crucial for maintaining the integrity of organizational assets. The “Detect” function in the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) provides essential guidance on implementing effective detection strategies.
With the release of CSF 2.0, the “Detect” function has received significant updates from its 2018 predecessor, reflecting advancements in detection technologies and methodologies. This blog post examines these changes, their implications, and how organizations can integrate these advancements into their cybersecurity practices.
Overview of the “Detect” Function
The “Detect” function focuses on the development and implementation of capabilities to promptly identify the occurrence of a cybersecurity event. It emphasizes the need for continuous monitoring and detection processes to ensure organizations can respond to threats swiftly and effectively.
Critical Updates in CSF 2.0
- Continuous Monitoring
One of the most prominent enhancements in CSF 2.0 is the emphasis on “Continuous Monitoring.” While the 2018 version of the CSF acknowledged the importance of monitoring, CSF 2.0 focuses on the need for continuous, comprehensive monitoring of all cyber assets and networks. This shift recognizes that the rapidly evolving threat landscape requires ongoing vigilance to detect threats as they emerge.
- Adverse Event Analysis
CSF 2.0 introduces “Adverse Event Analysis” as a new category within the “Detect” function. This change highlights the importance of detecting and analyzing events to understand their nature, scope, and potential impact. This analytical approach aims to enhance organizational abilities to differentiate between false alarms and genuine cybersecurity threats, enabling more effective and targeted responses.
Implications for Organizations
The “Detect” function updates in CSF 2.0 represent a strategic enhancement of detection capabilities, emphasizing the need for real-time monitoring and in-depth analysis of cybersecurity events. For organizations, these changes underscore the necessity of investing in advanced detection technologies and analytical capabilities to stay ahead of threats.
Adopting Continuous Monitoring Practices
Organizations looking to align with CSF 2.0 should prioritize implementing continuous monitoring solutions that offer real-time visibility into their digital environments. This involves utilizing advanced tools and technologies that can detect anomalies, unauthorized access attempts, and other indicators of compromise across networks, systems, and applications.
Enhancing Analytical Capabilities
Incorporating adverse event analysis into detection strategies requires organizations to detect threats and analyze and interpret the related data. This may involve training cybersecurity personnel in advanced analytical techniques or employing sophisticated security information and event management (SIEM) systems that can automate the process of event correlation and analysis.
Conclusion
The “Detect” function enhancements in CSF 2.0 reflect a deepened understanding of the complexities involved in promptly identifying cybersecurity threats. CSF 2.0 guides organizations toward more proactive and intelligence-driven detection strategies by emphasizing continuous monitoring and adverse event analysis.
Adapting to these changes will be critical for organizations aiming to enhance their cybersecurity posture and resilience against the ever-evolving threat landscape. The journey towards achieving this level of detection proficiency will require a commitment to technological advancement and a culture of continuous improvement within the cybersecurity domain.