Fortifying Cybersecurity: Unpacking the Enhancements in CSF 2.0’s ‘Protect’ Function
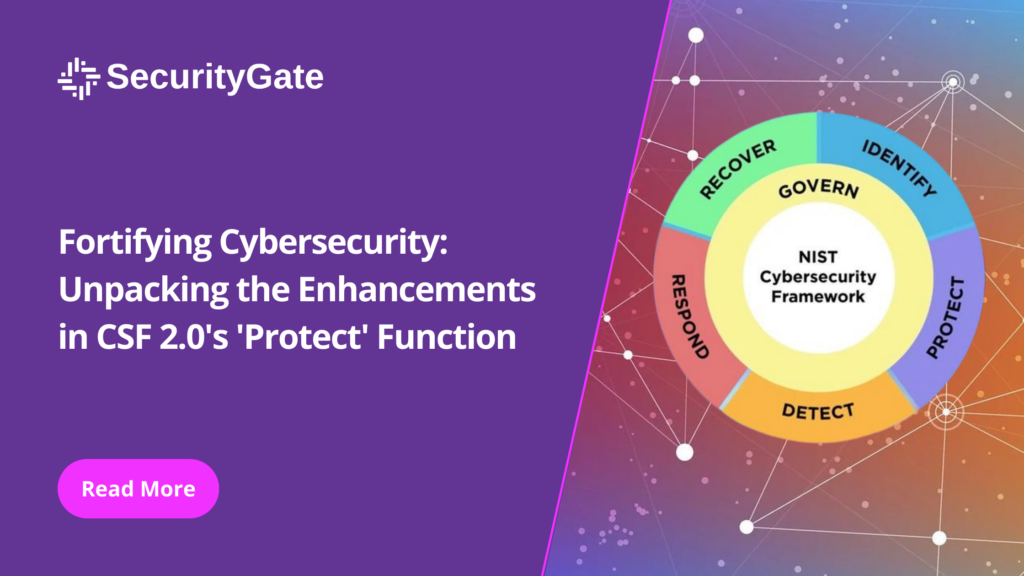
The need for robust cybersecurity measures has never been more apparent in the rapidly advancing digital landscape. With cyber threats becoming increasingly sophisticated, the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) 2.0 arrives as a beacon of guidance for organizations striving to bolster their defenses. The “Protect” function, a cornerstone of the […]
Deep Dive into the “Identify” Function: Transitioning from the 2018 Framework to CSF 2.0
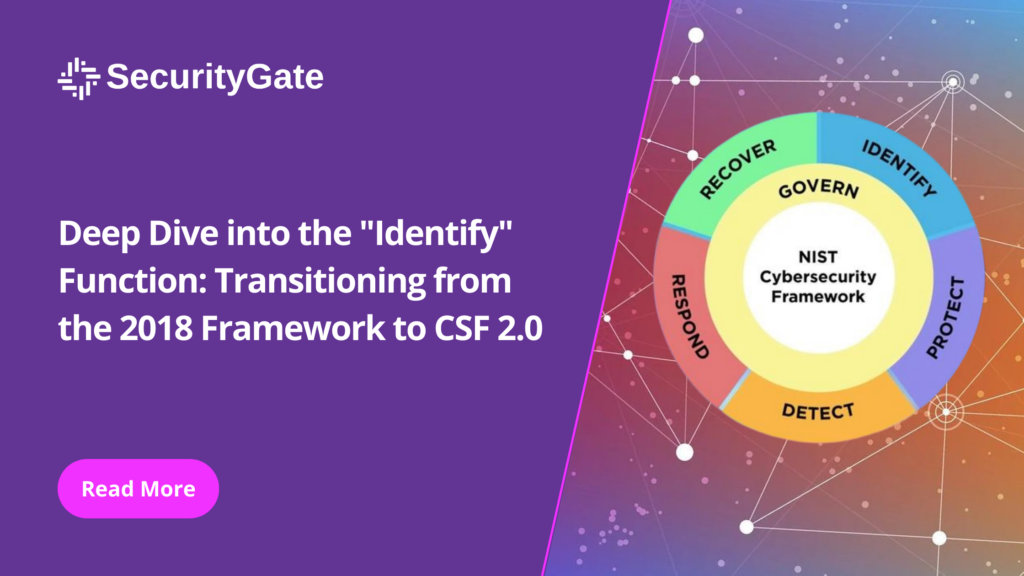
Understanding an organization’s digital assets and systems in the ever-changing cybersecurity landscape is crucial to ensure effective security. The “Identify” function of the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) serves as the foundation for this understanding, guiding organizations in establishing a comprehensive view of their cybersecurity posture. With the transition […]
The Evolution of the Govern Function in the Cybersecurity Framework: A Closer Look at CSF 2.0
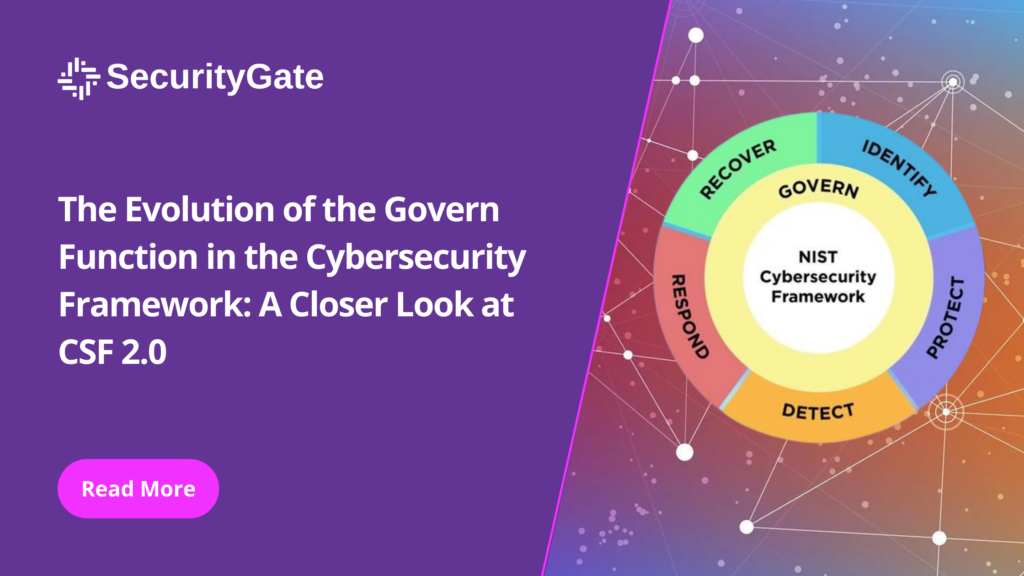
In the realm of cybersecurity, staying ahead of threats necessitates not just reactive measures but a proactive and structured approach to safeguarding digital assets. The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) has been a cornerstone for organizations striving to achieve this level of preparedness. With the introduction of CSF 2.0, several […]
Unpacking CSF 2.0: Navigating the Cybersecurity Landscape

In the fast-evolving world of cybersecurity, staying ahead of threats requires constant vigilance and a robust framework for managing risk. The National Institute of Standards and Technology’s (NIST) Cybersecurity Framework (CSF) has long stood as a beacon for organizations seeking to fortify their cyber defenses. With the release of CSF 2.0, NIST has introduced significant […]
The Crucial Role of Training in Enhancing Operational Technology (OT) Environments

In today’s fast-paced and interconnected world, Operational Technology (OT) environments are the backbone of various industries, from manufacturing to energy. Operational Technology (OT) is a critical component of industrial operations, encompassing both hardware and software that work in tandem to monitor and control physical devices. Its significance lies in its ability to drive and optimize […]
Advanced Ransomware Prevention in Industrial Control System Environments

Industrial control systems (ICS) that operate critical infrastructure are high-value targets for ransomware adversaries. Old SCADA (supervisory control and data acquisition) devices, PLCs (Programmable Logic Controllers), DCS (Distributed Control Systems), and other ICS components in critical infrastructure lack security controls and are vulnerable to attacks. Mitigating ransomware risks in ICS environments requires a multi-layered strategy […]
The Importance of Scoping Before Assessing Cybersecurity in IT/OT Environments

As organizations integrate information technology (IT) and operational technology (OT) systems, it becomes critical to evaluate cybersecurity risks across the entire connected environment. However, before you can effectively assess cybersecurity, it is essential to scope the evaluation properly. Rushing into an assessment without careful scoping can lead to incomplete results, wasted effort, and missed threats. […]
Panel: Defining the ROI of a Cybersecurity Strategy for the O&G Industry

I recently participated in the “Cyber Threat: Defining the ROI of a Cybersecurity Strategy for the O&G Industry” panel discussion at Digital Oilfields USA. The panel gave the audience insights on dealing with ransomware, employee training, and utilizing technologies to protect critical infrastructure. It was a pleasure to collaborate with Mex Martinot […]
How to Quickly Use the AESCSF Assessment Framework
What is the AESCSF Framework? In 2017, the Australian government set out an initiative to strengthen the country’s cybersecurity posture and created the AESCSF. The framework went under revision in 2019, and again in 2020. Though no major changes were made in 2020, the revision came as part of Australia’s Cybersecurity Strategy 2020, which has […]
Solar Winds’ Orion Platform Hack Looks Like It Started With Simple Human Error

A brief (high level view) summary of what happened: A group of hackers were able to add disguised malware into a system in Solar Wind’s Orion Network Management Platform that pushes out updates to organizations who use Orion. When the compromised Orion system pushed out the update, the organizations who received it were unable to […]