MOVE FASTER THAN YOUR THREATS
Get rid of the countless spreadsheets, email chains, portals and apps. Bring every activity for industrial cybersecurity into one pane of glass.
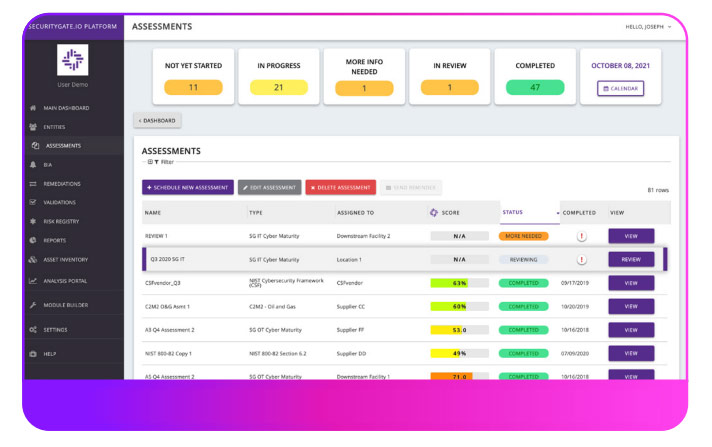
Framework Assessment Workflows
No spreadsheets needed. Everything happens inside our secure portal.
Allow internal team members and 3rd party vendors to collaborate through a secure, limited-view portal and track their progress.
Assessment data is automatically turned into reports for viewing and download on demand.
Keep respondents on track and on time with automatic notification reminders.
Store supporting documents in one location. Quickly access them for validation activities and audits.
Quickly start with 20 industry frameworks already available in the platform
Module Builder
Create your own custom frameworks to go above and beyond compliance. Start from scratch or create your own by mixing and matching questions from existing industry frameworks.
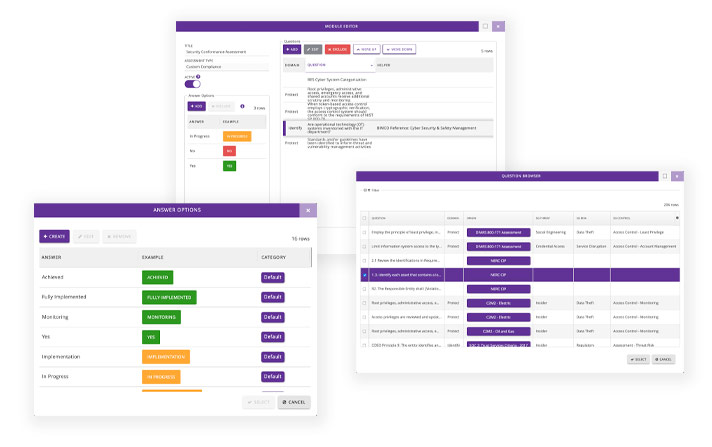
Define your response types and re-order the questions until your ready to send out the assessment.
Choose from our library of 20 industry frameworks, upload your own file, or start from scratch.
Business Impact Analysis
Business Impact Analysis (BIA) is designed to complement risk assessment efforts as a step in the process of showing business leaders how the outcome of an assessment relates to operations.
Choose from 4 different scenarios:
- Ransomware Attack
- Supply Chain Attack
- Insider Threat
- Unscheduled Technical Disruption
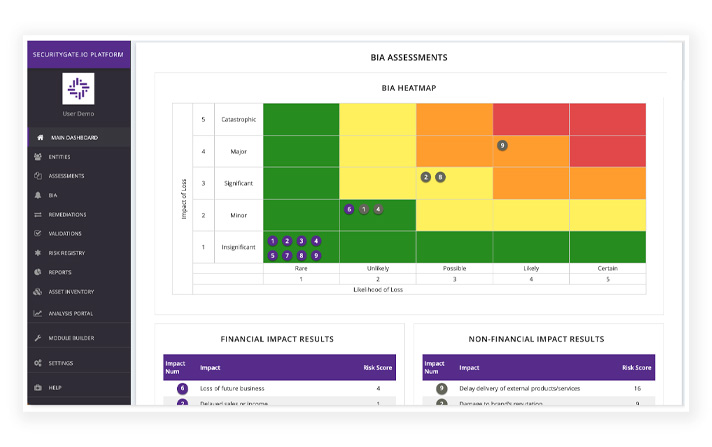
View your highest areas of criticality with a heatmap report.
Measure the potential financial impacts to your organization within a given scenario.
Share results with stakeholders by accessing fully automated reports after completing a BIA.
Remediation Workflows
After an assessment the SecurityGate.io platform ties the missing controls* to a collaboration workflow that guides involved parties through remediation and improvement processes while giving top-level visibility to leadership teams.
Dashboards and a variety of automated reports provide on-demand, real-time tracking data and an analysis of security posture improvements and compliance progress.
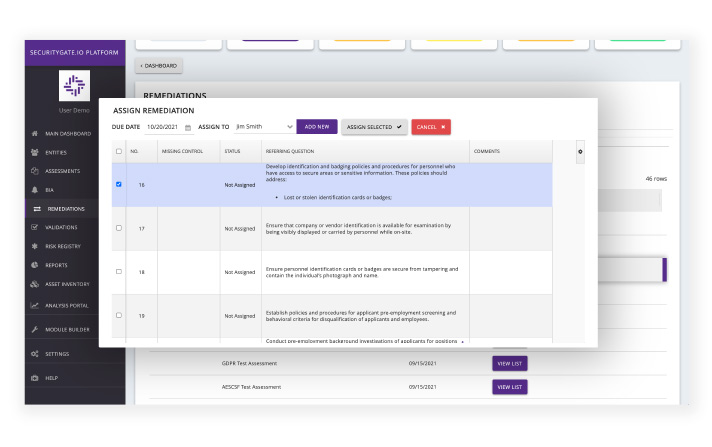
Assign remediation tasks to a single person or to many people.
Add comments, ask questions, and upload validating documents.
Gain clear insight into which missing controls are not actively being worked on along with documentation of who accepted the associated risks.
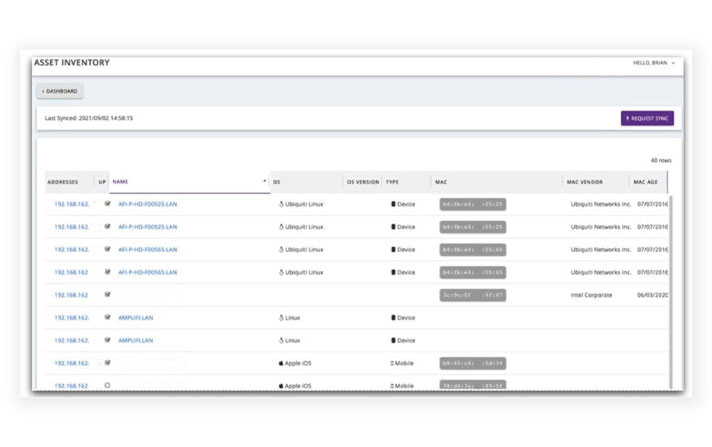
Asset Inventory Viewer
Display a comprehensive inventory of assets on a network. An asset inventory is a common control that is assessed for. With this integration, validations can be performed and logged without needing to leave the assessment in progress within SecurityGate.io.
Currently, we have pre-built integrations with Rumble.run and Tenable to automatically import this data into the SecurityGate.io platform.
Entities Dashboard
An entity is anything you’re assessing (i.e. an entire organization, a client, a facility, a network, or even an individual system component.)
View the risks posture of your “entities” in real time spot trends in growing risk.
The Entities Dashboard provides a fully contextualized view of what risk looks like today across the organization and helps with forecasting what it will look like tomorrow.

View data from asssessments, remediations, compliance, maturity, and security posture in a single pane of glass.
Easily view the severity of risk or the degree to which the entity is compliant or not.
Reports
Track risk and risk management activities in one place.
Easily share data with pre-formatted reports including executive summaries, audits, and comparisons. Export reports in pdf or .doc format for quick edits.
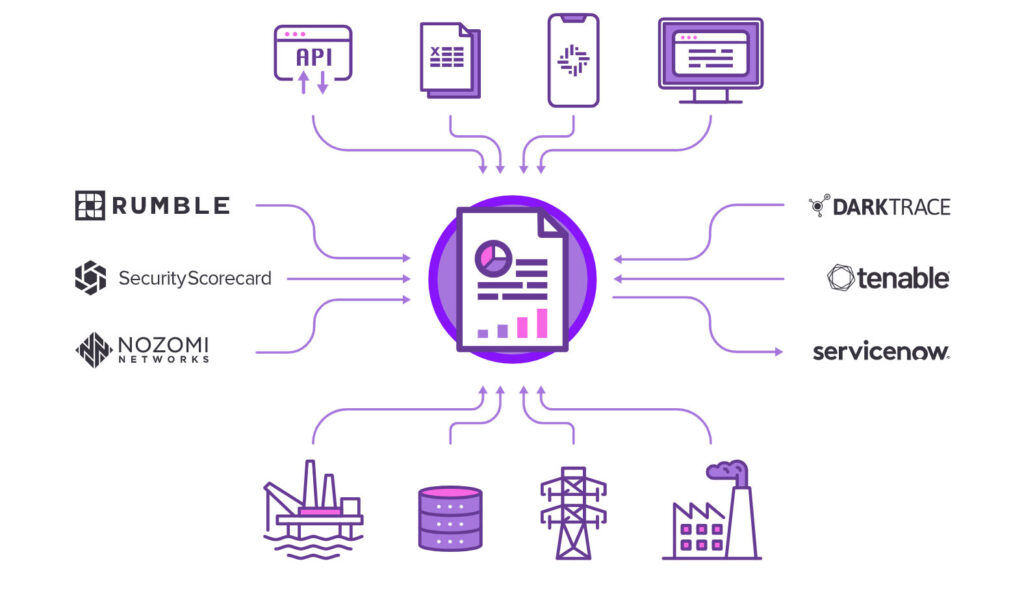
Portfolio Analysis
Between security systems and risk management activities, most companies have more cybersecurity data than they know what to do with. The Portfolio Analysis tool makes it easy to understand what’s important in your data.
Identify trends, spot outliers, and benchmark progress across clients and facilities.
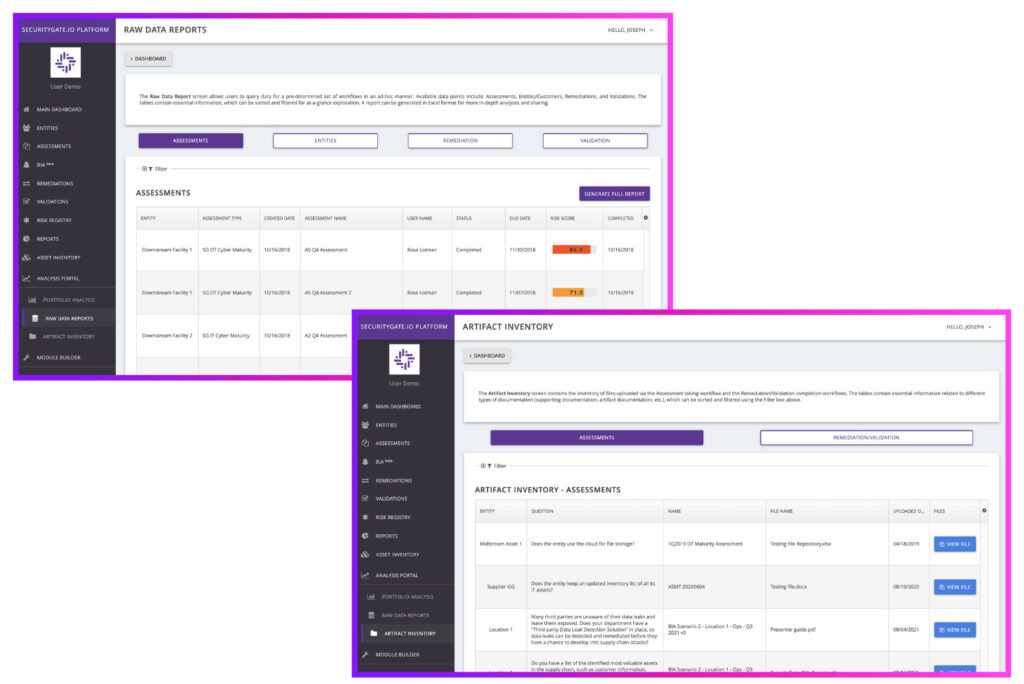
View, sort, and review it all from within the platform, or export a cleanly formatted copy of your data in a .CSV for external analysis.
Open API
- /entities - query a list of entities in your account. Entities are the facilities/business units/assets/etc assessed for risk and compliance.
- /entities/{entityId}/assessments - - provides a list of the assessments under a specific entity
- /assessments/{assessmentId}/remediations - see a list of remediations for a specific assessment
- /assessments/{assessmentId}/validations - shows a list of validations for a specific assessment
- /remediations/search - search for information on the entity, assessment, or remediation in your account
ot_systems_online = true;
while (ot_systems_online) {
UseSecurityGateio( );
PerformCyberAssessment( );
SeeSecurityRisks( );
FollowSecurityGateioSteps( );
GainStrongerCyberSecurity( );
AvoidOTSystemsBreach( );
}
Availability & Tech Stack
- Manage all facilities and clients from a single account.
- Provide limited access views for 3rd parties and internalstakeholders: View important metrics and reports, respond to assessment questions, collaborate in remediation efforts
- Secure cloud environment hosted with Amazon Web Services
- 2 Factor Authentication secures user access
- All data is encrypted by default
- Optional ability to bring your own encryption key(s) for further data security

- Access for assessment responses for those working in remote areas in low/no cell coverage.