#DeleteTheSpreadsheet
NERC-CIP Assessments Made Easy
See how your team can ditch spreadsheets and PDFs forever
THE BETTER WAY FOR TEAMS TO MANAGE OT/ICS RISK.
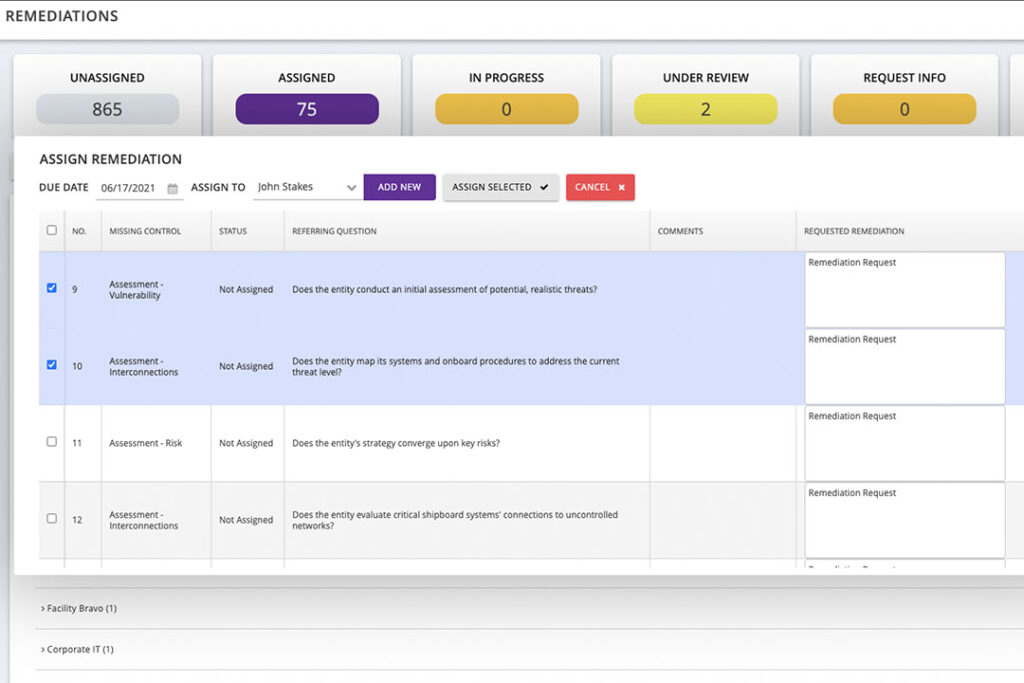
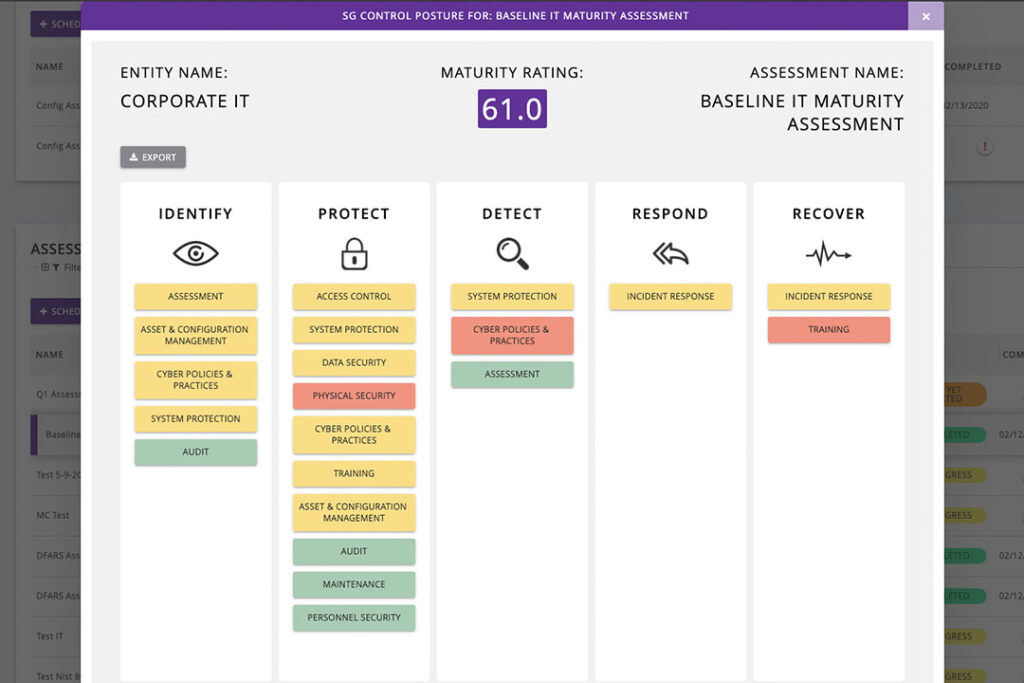
Find all the gaps easier
Replace the slow, disruptive, assessment processes and finally #DeleteTheSpreadsheet with fast SaaS workflows & reporting automation.
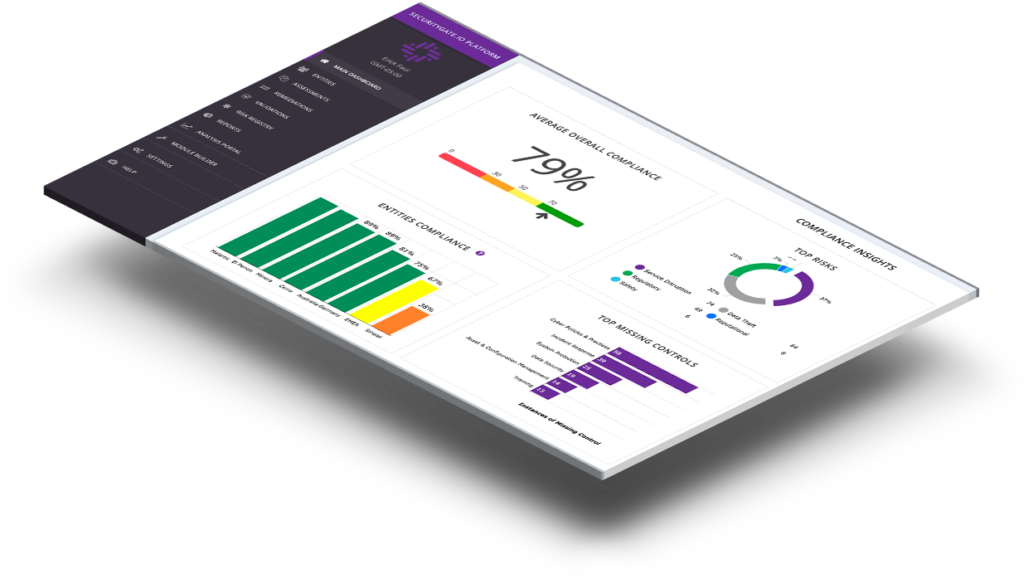
Make the right decisions faster
With consistent reporting, you can align your team on next steps and provide leaders with data they can trust to make decisions faster.
See your next steps prioritized


Start instantly with the pre-configured NERC-CIP framework.
We’ve done the hard work for you. Start assessing your facilities against the NERC-CIP framework for industrial risk management.
Complete an assessment in as little as 2 hours and understand exactly where your organization’s risks are with the ability to break down assessment results by each section/control.

Find a Consultant
Looking for someone to help you manage your next NERC-CIP risk assessment?
We partner with experts in critical infrastructure to help organizations maintain security. Click below to start a form and we’ll find you a match within our network of consultant partners.
Explore Resources

Cybersecurity Benchmarking for Critical Infrastructure Sectors
3 Challenges to Industry Benchmarking It was an honor to be invited by the Capital Factory to meet with CISA’s Infrastructure Security team and address

SecurityGate.io Reports Accelerated Company Growth As Industrial Cybersecurity Market Takes Off
SecurityGate.io reports 200% growth in sales & marketing headcount over the last six months to support a 329% increase in new sales requests over the

Bill Lawrence: Chief Information Security Officer
Bill Lawrence came to SecurityGate.io to serve as Chief Information Security Officer with an incredible background. In the announcement of Bill joining our team you

Module Builder Enhancements and Features for Consultants
June Product Updates This month’s release includes some exciting new updates to the SecurityGate.io Module Builder, which gives cybersecurity teams the flexibility to create their
Two-Factor Authentication
What is Two-Factor Authentication? Two-Factor Authentication (2FA) is a security process in which a user provides two different authentication factors to verify themselves when logging
Bring Your Own Key Data Encryption
What is it? Bring Your Own Key (BYOK) is a feature that enables account administrators to protect the data uploaded to the SecurityGate.io platform using