ISA/IEC 62443 comprises a collection of global standards for industrial automation and control systems. These standards set out a complete range of criteria for creating, executing, and maintaining secure industrial systems. This article emphasizes the significance of implementing ISA/IEC 62443, specifically standard 3-2, to understand the risk composition of your zones and conduits. We will also delve into the benefits of utilizing these standards and how SecurityGate’s Platform integrates with them, creating a seamless framework for practitioners to achieve your companies’ objectives.
What is the ISA/IEC 62443 series of standards?
Each industrial automation and control system (IACS) presents a different business risk depending on threat exposure and likelihood. Inherent system vulnerabilities pose various consequences if compromised. Therefore, every organization that owns and operates an IACS has a different risk tolerance. Finding that current IT standards and practices were insufficient to ensure the safety, integrity, reliability, and security of IACS, the International Society of Automation (ISA) updated its ISA-99 standard in 2002 and has come to be known as ISA/IEC 62443.
The international standards provide a comprehensive framework for designing and implementing secure industrial automation and control systems. Considering that equally protecting all assets is not reasonable for risk management teams, the framework provides a risk-based approach to cyber security in which users prioritize vulnerabilities. The standard series is arranged into four sections: General Section (62443-1-X) includes the general topic common across the entire series. Policies and Procedures Section (62443-2-X) provides guidance for IACS Security policy and procedures. Section 3, System Requirements (62443-3-X), is the third group and covers the application of specific technologies in a control system environment. This section includes 3-2 security risk assessment for system design. Finally, section 4, Component, document information associated with developing IACS products.
Why Use ISA/IEC 62443-3-2 for Securing Industrial Automation and Control Systems?
The 3-2 standard includes a set of engineering measures that are a common requirement among stakeholders to guide organizations through IACS risk assessment and applying countermeasures to enhance security. This includes meeting component requirements (CRs), which contain improvement requirements (IRs). Companies who certify their products to these standards through organizations such as ISASecure, benefit from a reduced chance of cyber attack, improved security throughout the lifecycle, and reduced overall cost. As IACS owners identify threats higher than their established tolerable risk, they can prioritize efforts to ensure that their networks, applications, and processes are secure, resilient, and operationally sound.
Implementation Challenges with the ISA/IEC 62443 Standards
While the standards’ breadth and depth help address many business issues, implementation is a serious undertaking. Since ISA/IEC 62443-3-2 is not questionnaire-based, there’s no typical way to apply it. Assessments can vary by scope, including what environments a company wishes to identify, the likelihood and consequences of cyber attacks on those assets, and how they’d like to apply mitigation controls. Even the most mature companies want to define how best to apply the 62443-3-2 standards. Challenges are around the prework needed to perform an assessment like agreed-upon Risk Matrix that includes likelihoods, consequences, and impacts. The first assessment is crucial for determining the importance of the asset being evaluated. This evaluation process prioritizes and identifies critical factors using tools such as PHA scores and screening questions.
Many businesses are now adopting the ISA/IEC protocols, and our SecurityGate Platform simplifies the implementation of ISA/IEC 62443-3-2 framework. Our platform offers an easy-to-follow workflow that allows teams to input their specific scenarios, consequences, threats, and mitigating controls based on their IEC profile. With our structured and automated approach, management teams can assess risk at a granular level and aggregate the overall mitigated and unmitigated risk scores for each system. This makes SecurityGate a trusted repository for systems under consideration, the risks they pose, and the mitigating controls in place, promoting accountability for risk treatment.
How to Simplify an ISA/IEC 62443-3-2 Risk Assessment
One point of confusion is that ISA/IEC 62443-3-2 doesn’t specify the steps teams should take. SecurityGate has interpreted the framework and translated the workflow into assessments in our Platform, allowing users to select what they’d like to assess and the questions they will use in a straightforward fashion.
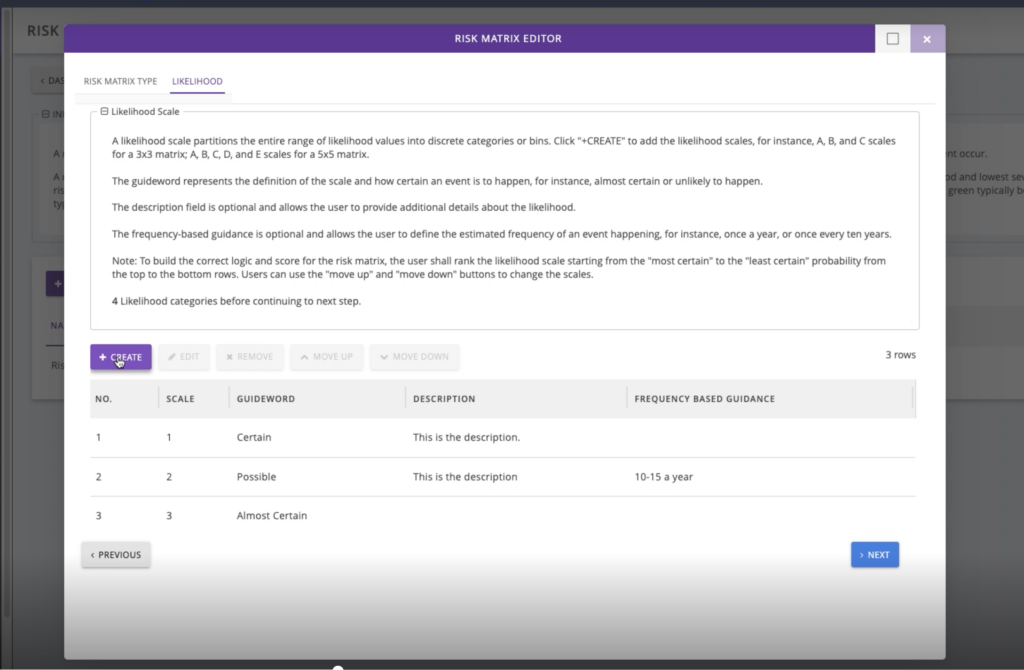
We understand that each company has its unique way of conducting risk assessments. Therefore, we have developed customizable workflows that cater to specific business needs. Our default IEC risk matrix types are available, and you can perform steps based on your specific requirements.
The SecurityGate Platform automatically compares your current security level to your company’s target level and generates results that provide valuable insights. This helps you determine your security score. This helps eliminate the tedious and time-consuming task of manually selecting data from spreadsheets or PDFs.
Conducting an ISA/IEC 62443-3-2 Assessment with the SecurityGate Platform
Prior to performing an assessment in the SecurityGate Platform, companies will begin by defining their scope including what assets they’d like to assess and the business tolerance level they’d like to measure against.
ISA/IEC 62443 establishes requirements for defining a system under consideration (SuC) for industrial automation and control, and partitioning the SuC subject into zones and conduits.
Choose Your Facilities
Users can assign assessments to facilities virtually, specifying what zones and conduits to assess and defining tolerable levels of risk within the Platform to create a risk matrix with predefined goals that the assessment will measure against.
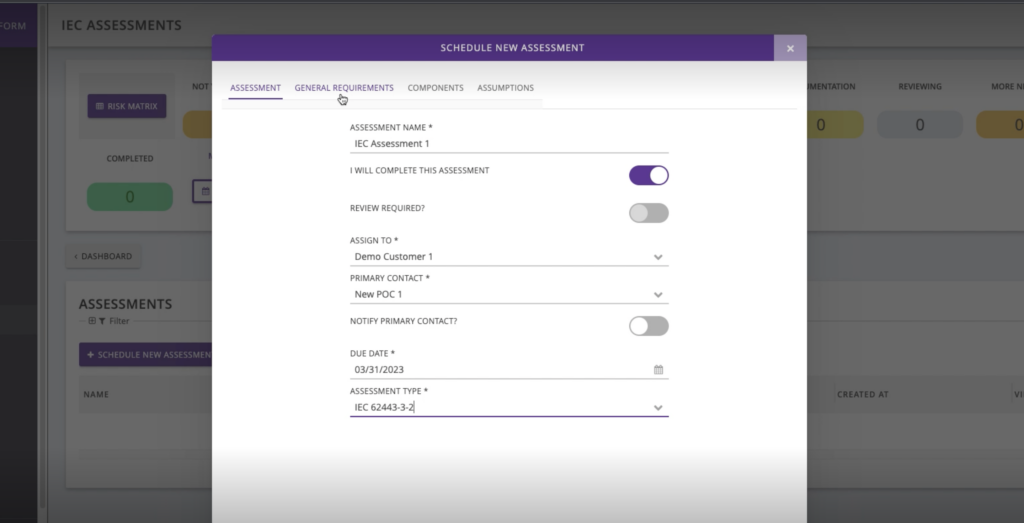
Schedule a new assessment
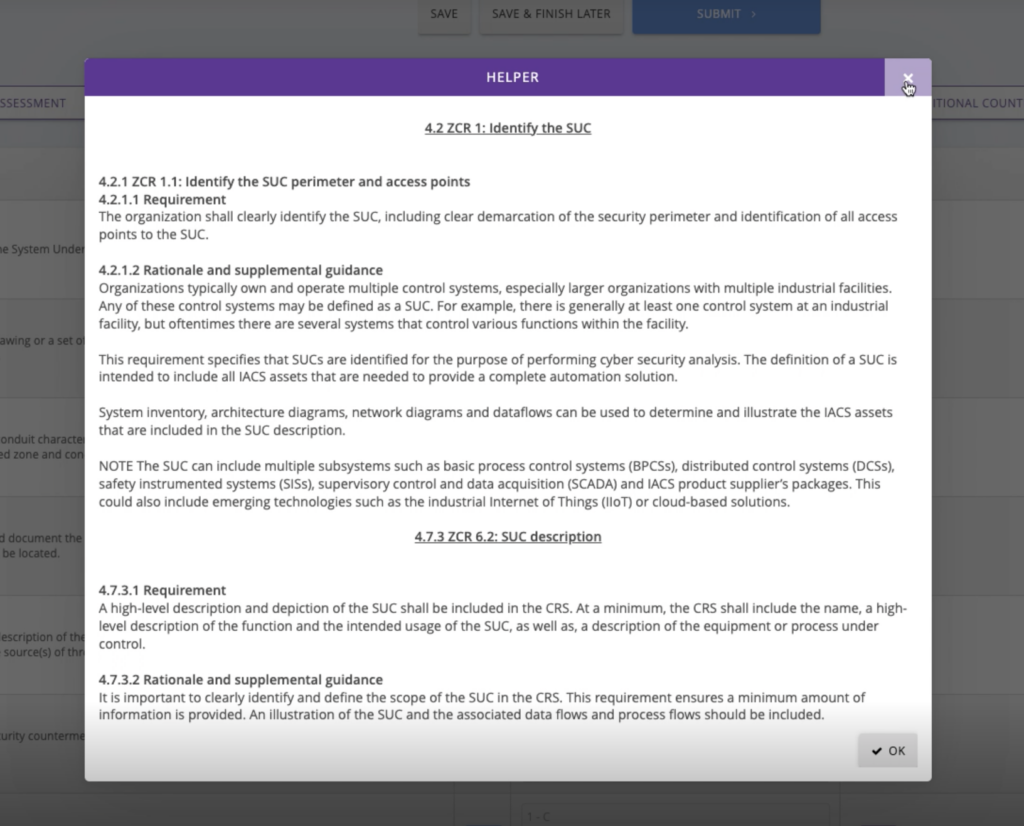
Users will begin their assessment with an introduction tab that explains what to expect and how scoring works. Helper text makes it easy to follow along with each step and understand the portion of the 62443-3-2 requirements you’re adhering to at different points along the workflow.
Configure your Categories
The next step is to assess the consequences and likelihoods for zones and conduits, including your target security level for each.
Determine Impact
From there, you can define the severity of the risk by evaluating it in light of the controls put in place and comparing the security level to the target security level.
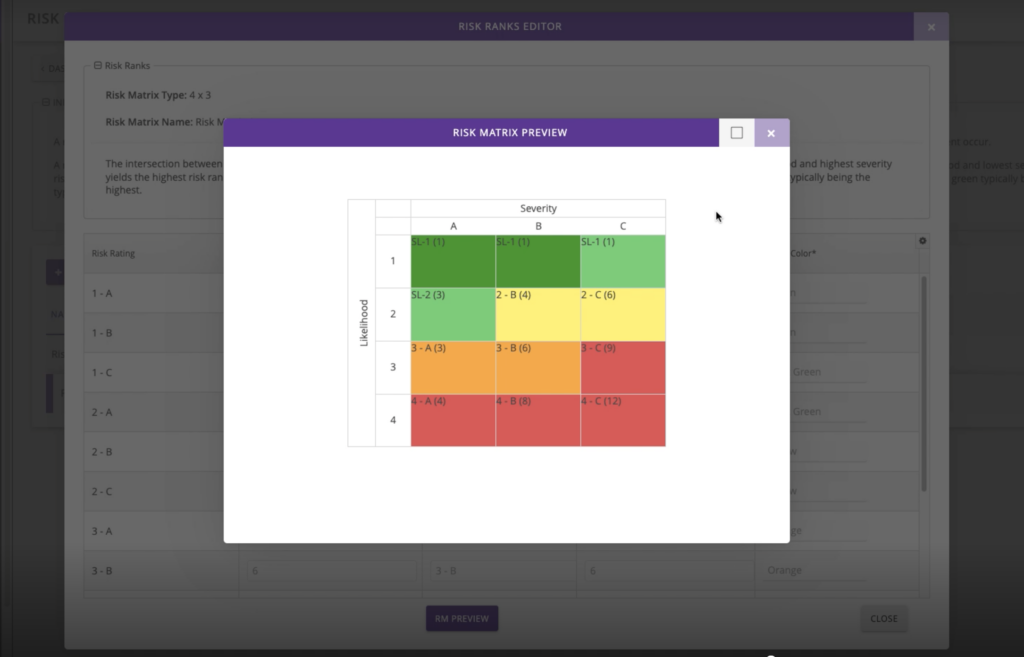
Assessment results are captured in a heatmap. Once you finish the IEC 62443-3-2 assessment, your threats will be populated across the heatmap according to their likelihood and severity.
If done manually, measuring risk across multiple systems can take an immense amount of time. The SecurityGate Platform digitalizes this process, automatically analyzing the risk of threats for fast results.
Identify countermeasures
Companies can compare the risk scores of all their systems to prioritize resources and develop plans. Businesses will vary in how they use their results. Some will work to mitigate risk until it reaches a tolerable level or becomes non-existent. Others will consider taking additional steps in another workflow, or even accept the risk and end the workflow without working toward target security levels.
Conclusion
ISA/IEC 62443 family of standards provide a comprehensive set of standards to ensure companies can secure industrial systems. By utilizing Standard 3-2, potential risks in zones and conduits can be accurately assessed and remediated. Any company, regardless of its level of maturity, can reap the benefits of using the ISA/IEC 62433 workflow on the SecurityGate Platform. Our forward-thinking implementation provides historical documentation in a cloud-based environment, automated insights and reports, and connectivity to other Platform workflows such as remediation and risk register. By consolidating all assessment actions, outputs, and remediation activities in a single platform, completing IEC assessments can add significant value to your company.
As a technical member of ISASecure, we actively participate in weekly member meetings and help shape the direction and development of the ISASecure conformance specifications, allowing us to consistently update and improve our workflows along with the latest updates.
Contact our expert team for help using the ISA/IEC 62443-3-2 workflow on the SecurityGate Platform.