Implementing MITRE tactics into your risk management process is important to help determine where to spend time and budget into making improvements that maximize the efficacy of your program. However, doing so can be complex and time-consuming. This post will explore how you can tie your risks to MITRE tactics by simply running a framework-based assessment.
Get Familiar with MITRE ATT&CK ICS Tactics and Techniques
The MITRE ATT&CK framework serves as an open, free globally-accessible knowledge base of known adversarial techniques, or hacks. These techniques are based on real-world observations, which makes MITRE especially practical for analyzing how an attack could be carried out within your own infrastructure.
The techniques are organized into a set of tactics using a common language to enable a standardized way for security teams to understand all possible hacker execution methods and communicate regardless of the asset or system type.
What are MITRE ATT&CK Tactics?
The MITRE framework includes 12 industrial control system (ICS) tactics that represent the “why” of an ATT&CK technique. In other words, the tactics represent the adversary’s tactical goal, the reason for performing an action, such as achieving credential access.
What are MITRE ATT&CK Techniques?
Techniques, on the other hand, represent “how” an adversary achieves a tactical goal by performing an action. For example, an adversary may dump credentials to achieve credential access.
ATT&CK data is collected through publicly available threat intelligence and incident reporting. MITRE also uses public research on new techniques that closely align with common adversary behavior. ATT&CK adds value by providing a tangible and consistent framework for assessing and discussing security in a way that reflects real-world adversary behaviors.
In an effort to stay current with widely recognized industry standards, SecurityGate has updated the Top Threats report in our Platform to align with current MITRE ATT&CK ICS Tactics. This enables SecurityGate clients to enjoy the benefits of incorporating the knowledge of other security teams and researchers around the world. With this insight, SecurityGate users are empowered with the data they need to effectively prioritize remediations through their existing assessments.
Assess Your OT/ICS Facilities Against a Standard/Framework
SecurityGate has mapped these 12 MITRE tactics for ICS to commonly used frameworks to easily determine vulnerabilities without additional effort. All you need to do is complete an assessment across any of your facilities, which can be done within the SecurityGate Platform.
Once you’ve completed your risk assessment(s), a report is automatically generated which displays your top threats into MITRE threat groups. Your assessment responses trigger highlights of your vulnerabilities on your dashboard radar map and in your reporting, making it simple to identify and prioritize your greatest risks in little time and allocate resources accordingly.
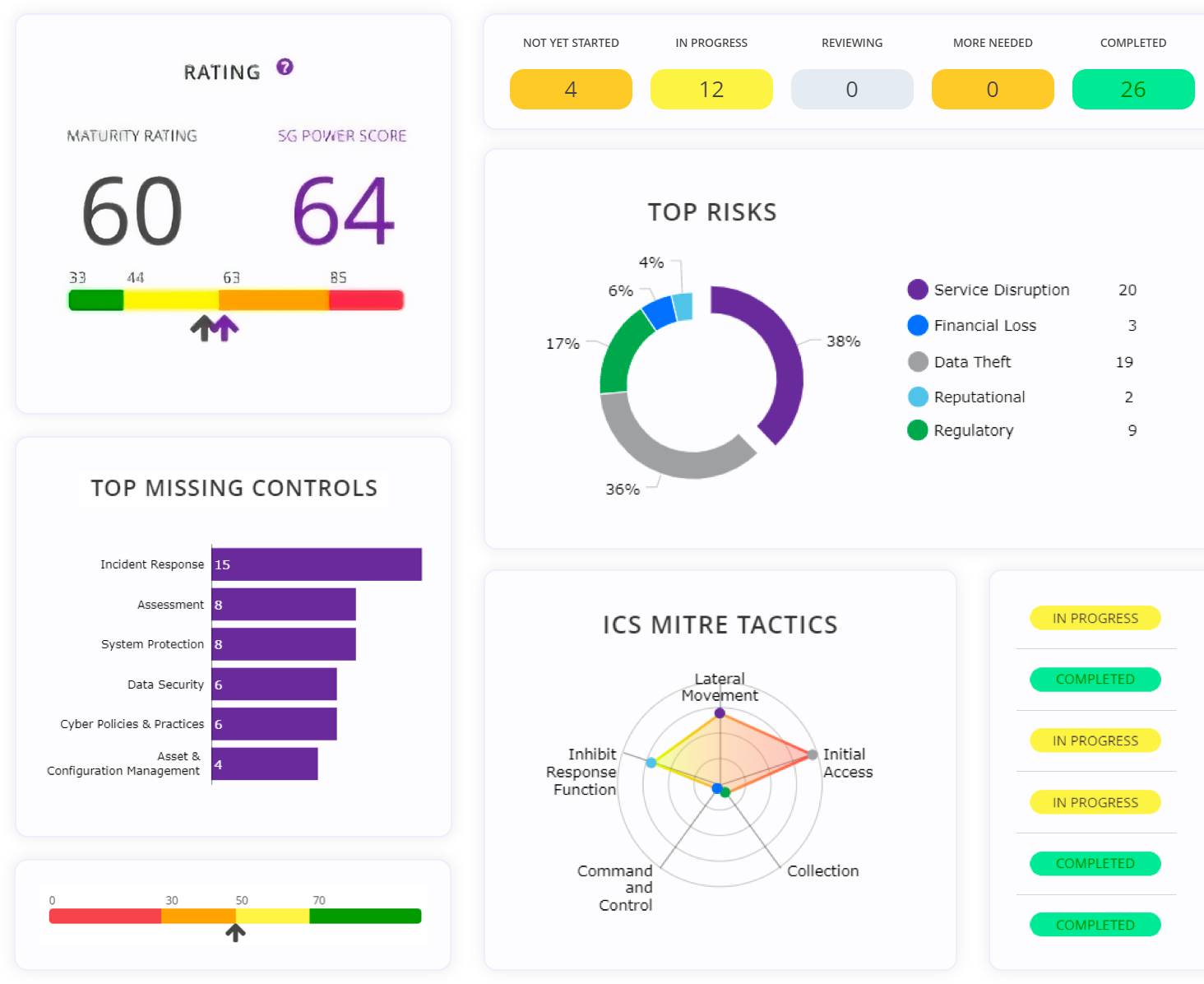
For example, if your assessment revealed that the control for Access Control was missing, the system would determine that you may be open to MITRE initial access, evasion, and privilege escalation threats.
Our unique mappings allow viewing the insight across multiple industry-leading frameworks, such as NIST CSF, NIST 800-53 Rev. 5 and CMMC to identify missing threats for assessments.
SecurityGate is continuously mapping frameworks to assessments to provide users with up-to-date insight as threats evolve and will include MITRE threat maps to these frameworks in the near future:
● Cyber security Maturity Model Certification (CMMC)
● DFARS 800-171 Assessment
● NIST 800-53 Rev. 5
● NIST 800-82 Section 6.2
● NIST Cyber Security Framework (CSF)
● NIST Cyber Security Framework (CSF) V1.1 – Compliance
● NIST Cyber Security Framework (CSF) V1.1 – Maturity
● SOC 2: Trust Services Criteria – 2017
● TSA Pipeline Cyber security Measures – Baseline
● TSA Pipeline Cyber security Measures – Baseline + Enhanced
The SecurityGate advantage
Risk assessment teams need to consider all possible data that could indicate a threat to their asset or system’s security. The collective knowledge encompassed in MITRE ATT&CK provides critical cyber threat intelligence.
SecurityGate’s innovative SaaS platform enables cyber teams to use the latest MITRE ATT&CK data through simplified dashboards and actionable data workflows to bring cyber programs to maturity faster and easier than traditional manual methods. The SecurityGate Platform in combination with the critical infrastructure expertise of our team provides quantitative and qualitative insight for the most effective way for companies to develop strategies and mitigate risk.
To learn more, book a demo or reach out to our team to get started.






