SecurityGate.io Platform – Entities Page
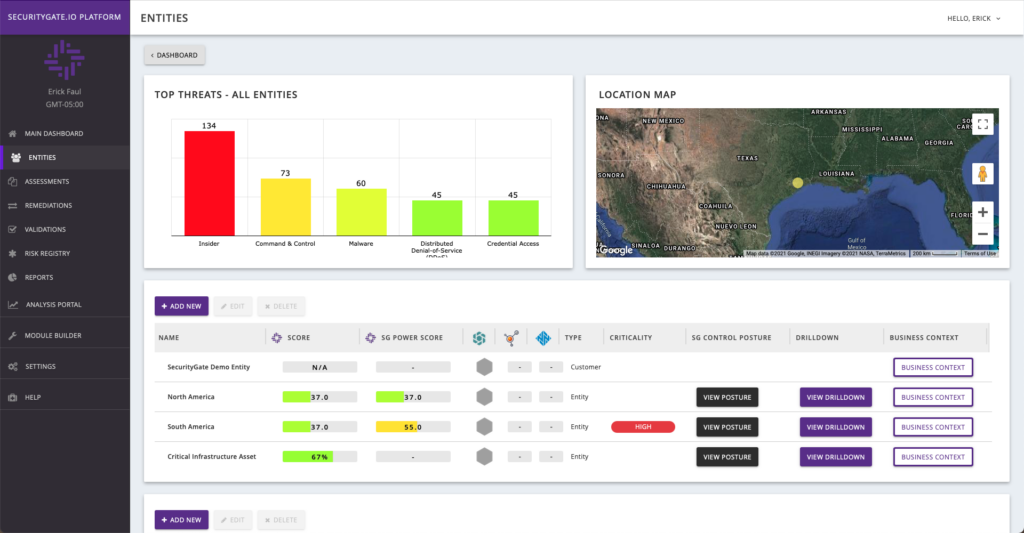
In this series of posts from our CEO and co-founder, Ted Gutierrez, he talks about our platform’s Entities Page. Why it exists, what our customers use it for, and how it helps them make risk management improvements faster. Enjoy. So You’ve Completed an Assessment….What Now? When I was a risk manager working for […]
The Most Overlooked Areas for Risk – Measure Cyber Risk Across People and Processes
Cybersecurity industry veterans Dave Bang and Mick Vaughan sat down to help us answer some major questions about why organizations often overlook the people component of risk, even though it’s the most critical area.
Plan Your Remediation Budget

Start with remediations first The most challenging part of remediations is finding the resources. Whether people, budget, or time, risk stakeholder teams are generally overworked and remediation activities tend to take second chair for newly organized or exhausted teams. One way to ensure that resources are available post-assessment is to ask for them before the […]
How to Pre-Plan Assessment Remediations

Make your assessments meaningful by pre-planning remediations Upon first glance, this may seem backward. Remediations come after the assessment where you discover what needs to be remediated, right? Yes, but if you’ve been involved with risk management for a few cycles of assessment and “reassessment” activities, you’re likely familiar with a common theme: Most post-assessment […]
How to Align Stakeholders on Your Cybersecurity Strategy

Overview We see that companies of all sizes often lack a strategy to gain buy-in from their stakeholders and thus fail to align on the purpose of assessments. Cyber risk assessments are a vital cornerstone of any risk management strategy. To make sure your organization is getting the maximum value of time and resources invested in these […]
10 Steps for a Successful Assessment Strategy

The key to successful assessment planning begins with clear communication throughout the initial planning phases. To ensure technical and non-technical leaders are aligned on the purpose of the cyber assessment, use the 10 steps below to facilitate communication prior to beginning the assessment. (Note: many of these steps can be done simultaneously.)
SecurityGate.io – Why We Started
In 2015 Russian operatives started a phishing process that hacked the U.S. presidential election. Continuing throughout the following year, leading up to the election, the hackers repeatedly stole data from Democratic National Committee servers and used it to influence voter behavior. Congress responded by passing the Cybersecurity Information Sharing Act and President Obama directed his […]
Top 3 mistakes made when going through a business impact analysis and how to avoid them
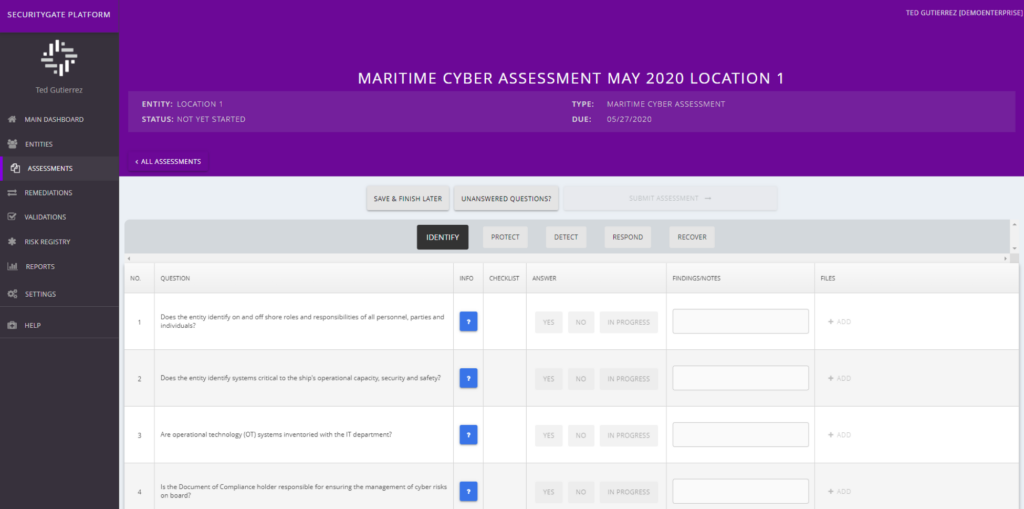
Edit: If you missed the LIVE show, don’t worry. We recorded it for you and have the video embedded at the bottom of this post. Or, if you prefer, listen to the podcast version on Apple and Spotify. When our customers are going through Business Impact Analysis (BIA) it’s pretty common for them to […]
Review of the Critical Infrastructure Maturity Model

The success and efficiency of any cybersecurity program depend primarily on how far people can see the difference between what situation they are in and what situation they think they are in. The Critical Infrastructure Maturity Model (CIMM) touches upon this critical issue.
Houston’s Veteran Business Support Network

SecurityGate.io was honored to participate in yesterday’s Veterans Day Pitch Event hosted by 1836. This event brought together a cross-section of leaders in Houston’s entrepreneurial community, venture capital, private equity, and industry sectors. This event both honors Veterans Day and provides support for veteran-owned start-up businesses.