Cybersecurity industry veterans Dave Bang and Mick Vaughan sat down to help us answer some major questions about why organizations often overlook the people component of risk, even though it’s the most critical area.
Why #CyberIsPeople
When high profile breaches happen, like the SolarWinds hack, the focus of the story is often about how specific technologies were exploited. Virtually zero coverage is spent on the processes that broke down leading up to the breach. In the case of SolarWinds, a password was never changed from the default, and ultimately it was a failure to follow this process that led up to the story we’re all so familiar with.
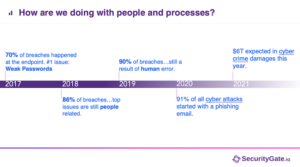
Cyber attacks are getting bigger, and more complex. Leaders often fall for the fallacy that if they just spend more on technology solutions to block and tackle, everything will be fine. Yet, people are increasingly at the center of attacks as years go by.
The Experts Weigh In
Dave Bang, Manager for Business Systems Security and is responsible for IT and OT Information Security for all LyondellBasell manufacturing facilities in North America lends his expert opinion on what companies can do to reverse this trend. Dave started supporting computers in 1993, moved into IT Security in 2006, and started partnering with OT Security in 2012.
Both Dave and Cyber SME, Mick Vaughan, have experience on both sides of the IT/OT fence. They offer unique insights into the question posed and offer advice on how to determine if your strategy is too heavily focused on technology.
Pitfalls of Not Putting Your People First
Humans are behind every piece of technology – the people who maintain it, operate it, and ensure that it is functioning correctly. “Point to any hack, and a majority of them have a people component,” says Dave. “There generally is a people failure or a process failure.” Without proper training, or if processes are simply skipped over, no single technology solution will be able to mitigate this kind of human error.
Dave recognizes that it’s not so easy to measure risk across people and processes. Some organizations measure it with budget spend, or with headcount, but these strategies still don’t take into account the skillset of personnel, where skills gaps may be, or how to fill those gaps.
“It’s much easier to buy technology, see the green lights are on and say that we’re getting value from it because it’s giving us data. It’s much harder to see the returned value of investing in employee training because it’s something you can’t see,” Dave notes.
Where to Find a Solution
Maintaining a robust cyber program takes everybody’s involvement. Listen in for advice on how organizations can effectively measure risk across their people and process, how managers can benefit from different strategies, and which industries are leading the way.