Top Three Reasons Standardizing Your Assessment Workflows Accelerates Your Cyber Journey

In an era where cybersecurity threats gain sophistication by the day, critical sector organizations are under increasing pressure to defend against these threats and do so efficiently and cohesively. One way to improve your organization’s defense is standardizing repeatable workflows that inform next-step actions. Standardization in cybersecurity assessments means establishing uniform processes, methodologies, and criteria […]
How to Connect a Cyber Risk to a Business Outcome

In today’s hyper-connected business landscape, continual cybersecurity improvement is a technical necessity and a cornerstone of sound strategic business operations. Yet, the journey from evaluating and recognizing cyber risks to effectively aligning them with business outcomes is fraught with challenges, particularly for Chief Information Security Officers (CISOs) striving to secure budgetary support for their cyber […]
Top 3 Strategies for CISOs and CIOs to Transfer Cyber Risk Effectively

Experienced CISOs and CIOs, having navigated at least one budget cycle, face the critical task of enhancing cybersecurity measures in their enterprises. This blog post delves into three pivotal strategies for effective cyber risk management: Comprehensively understanding organizational cyber risks Setting a universally comprehensible cybersecurity goal, and Fostering a culture of participation with incentives. It […]
Building an Effective Cybersecurity Risk Management Strategy on a Budget: Insights for CISOs and CIOs

Cybersecurity is a complex and challenging issue. As a CISO or CIO, managing it can be a daunting task, especially when resources are limited. However, crafting an efficient and effective risk management strategy is fundamental to ensuring the security of your organization’s information assets. This comprehensive guide offers practical steps and valuable resources that can […]
Top 3 Challenges Security Leaders Face in 2023-2024

Thanks for the opportunity to serve this great community of Security & Risk Management Leaders. Knowing the landscape of our #criticalinfrastructure sector challenges helps us plan and allocate resources effectively. I’ve had a great number of collaborations with industry leaders this quarter, focusing on interest rates, new threats, the evolution of AI, and global economies. Here are […]
A Letter from the CEO

Dear team, customers, and investors The challenges ahead for us collectively in 2023 are numerous: Global economic uncertainty. The worrisome expansion of the Ukraine/Russia conflict. The eternal challenges of scaling SaaS globally with a keen eye on efficiency and resource management. Undoubtedly such looming dangers in the cyber threat landscape call for asset owners to […]
Cybersecurity Benchmarking for Critical Infrastructure Sectors

3 Challenges to Industry Benchmarking It was an honor to be invited by the Capital Factory to meet with CISA’s Infrastructure Security team and address how to scale cybersecurity programs. I enjoyed giving a brief presentation on SecurityGate.io’s mission and how we are serving the critical infrastructure community. One of the questions I received was […]
Maritime Cybersecurity Risk Assessment Tool

Battling 21st Century Threats on the High Seas While historically pirates have been considered the primary threat to maritime security, increasingly ships and shipping have become vulnerable to cybersecurity threats. In particular, a number of the systems aboard vessels have been found to lack protection measures to safeguard ships from specific types of cybersecurity attacks. […]
How Successful Cybersecurity Consultants Drive Higher Client Satisfaction
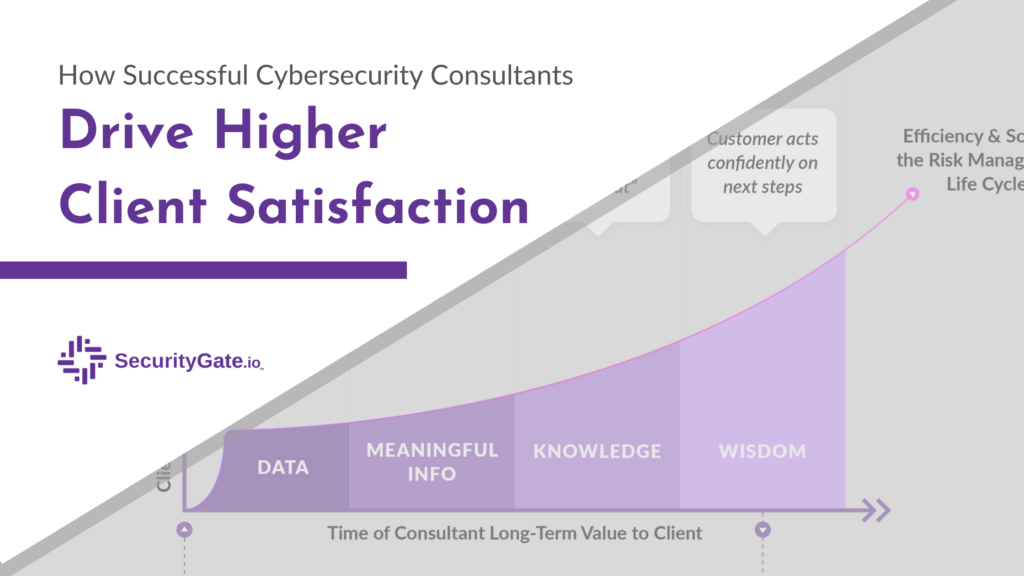
As an ex-assessor turned product company CEO, I believe great inventions spring from the minds of people hardened through their own struggles and challenges in a unique arena of expertise. For the team at SecurityGate.io, we’re a Software as a Service (SaaS) company, but if you ask our clients what we do they’ll likely say we’re […]
Colonial Pipeline Cyber Attack – Help With Cyber Assessment And Next Steps

On Friday Colonial Pipeline, a major U.S. fuel pipeline operator, was brought down by a ransomware cyber attack. Details are still coming in as the situation develops. We recognize how difficult this time is for the teams at Colonial Pipeline and all the vendors and suppliers that work with them. Our hearts go out for […]