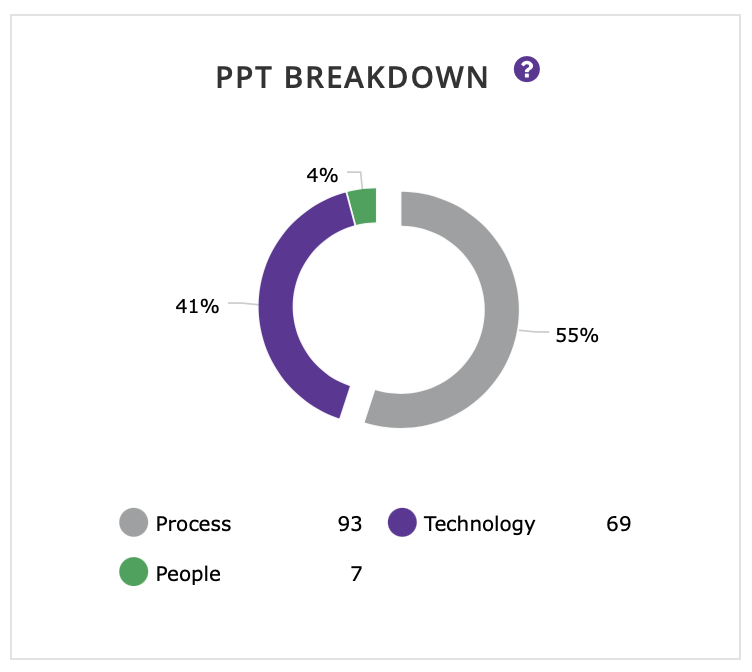
Today we would like to announce the release of the SecurityGate.io PPT (People Process Technology) Insight for immediate use in our cyber risk management platform.
The PPT Insight is a fully-automated, industry-first capability for understanding, organizing, and managing controls. It takes cyber assessment data and instantly shows how an organization’s missing controls (which often translate to cybersecurity risks) are categorized across their people, processes, and technology.
When leaders are better able to understand what mediums of controls are in place (or not), they’re better able to understand what needs to be improved as soon as possible vs. what can wait until later. In addition to categorization, the PPT insight shows how the risk of the missing controls are prioritized against each other, with regards to the unique context of an organization’s operation and use of its assets.
The SecurityGate.io PPT Insight gives security leaders an understanding of how controls relate to the three main components of cybersecurity: People, Process, and Technology. Many controls can span multiple categories. We’ve identified the primary drivers of the controls to emphasize which area(s) they impact the most, and calculate the severity of the risk across the categories. People – Controls primarily relating to and relying on people’s actions, behaviors, and knowledge. Process – Controls primarily in place through processes that have been built out for ongoing use. Technology – Controls primarily relying upon pieces of technology (spanning hardware and software) that are setup throughout an organization.
Why is this important?
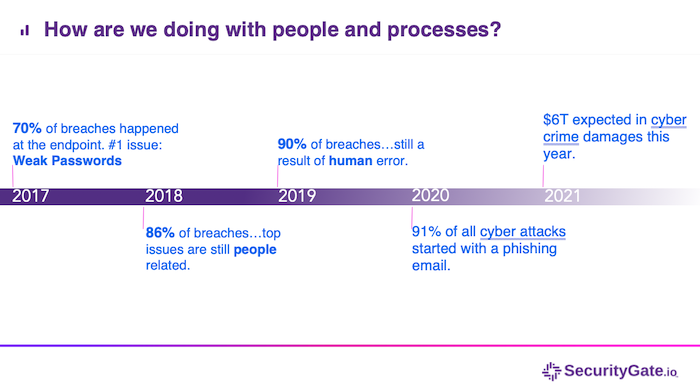
Cross-industry market data shows cybersecurity budgets are heavily invested in solutions that focus on technology controls, while people and process controls tend to receive less attention. At first pass, this may seem normal – it is. In the cybersecurity industry, we tend to think technology will be the best route to security. But the past years of cyber breaches have shown as many as 90% are due to a human/process issue. In fact, no matter what type of cyber attack, 91% of all attacks in 2019 going into 2020 started with a phishing email. The bad actors know people and processes are usually the easy way in. What our industry shows is an unhealthy imbalance in our cybersecurity strategies being overly focused on technology and under-invested in people and processes. The objective view of our PPT Insight gives security leaders the confidence they are focusing their time and budget in the right places at the right time. And that all cybersecurity tactics adopted are decided upon objectively and not necessarily based on subjective internal opinions, budget cycles, or industry trends.
#CyberIsPeople
Part of the challenge in security is gaining budget that addresses your needs holistically. Hackers take a holistic view of your operation to find the best attack vectors. Taking a holistic view of risk and risk assessments is the only way to address this and work towards operational resiliency. This means showing cyber is more than just technology. The PPT Insight gives a common language with supporting reports and dashboard charts for cybersecurity teams, operations, and business executives to use when discussing risk. This provides a simple way to make sure everyone understands the data and is on the same page with where to prioritize time and budget. We’re excited about the PPT Insight and what it brings to the industry. For more information and a demo, contacts us today.The SecurityGate.io PPT Insight gives security leaders an understanding of how controls relate to the three main components of cybersecurity: People, Process, and Technology. Many controls can span multiple categories. We’ve identified the primary drivers of the controls to emphasize which area(s) they impact the most, and calculate the severity of the risk across the categories. People – Controls primarily relating to and relying on people’s actions, behaviors, and knowledge. Process – Controls primarily in place through processes that have been built out for ongoing use. Technology – Controls primarily relying upon pieces of technology (spanning hardware and software) that are setup throughout an organization.
Download the Guide
Enjoy this content?
Get the comprehensive guide on how to improve your most overlooked area for risk.