Accelerate Your OT/ICS Cyber Maturity with SecurityGate
With more than 20 out-of-the-box cyber assessments and frameworks, SecurityGate is the only solution cyber security teams can trust to assess, improve, and document risk.
Purpose Built for Critical Infrastructure
Typical IT and GRC solutions lack the ICS expertise and the customization necessary to assess gaps and remediate issues for complex OT environments. As an OT-first, adaptable platform, SecurityGate is engineered to help cyber teams collaborate and make improvements faster.
Connect C-Suite and Cyber Leaders
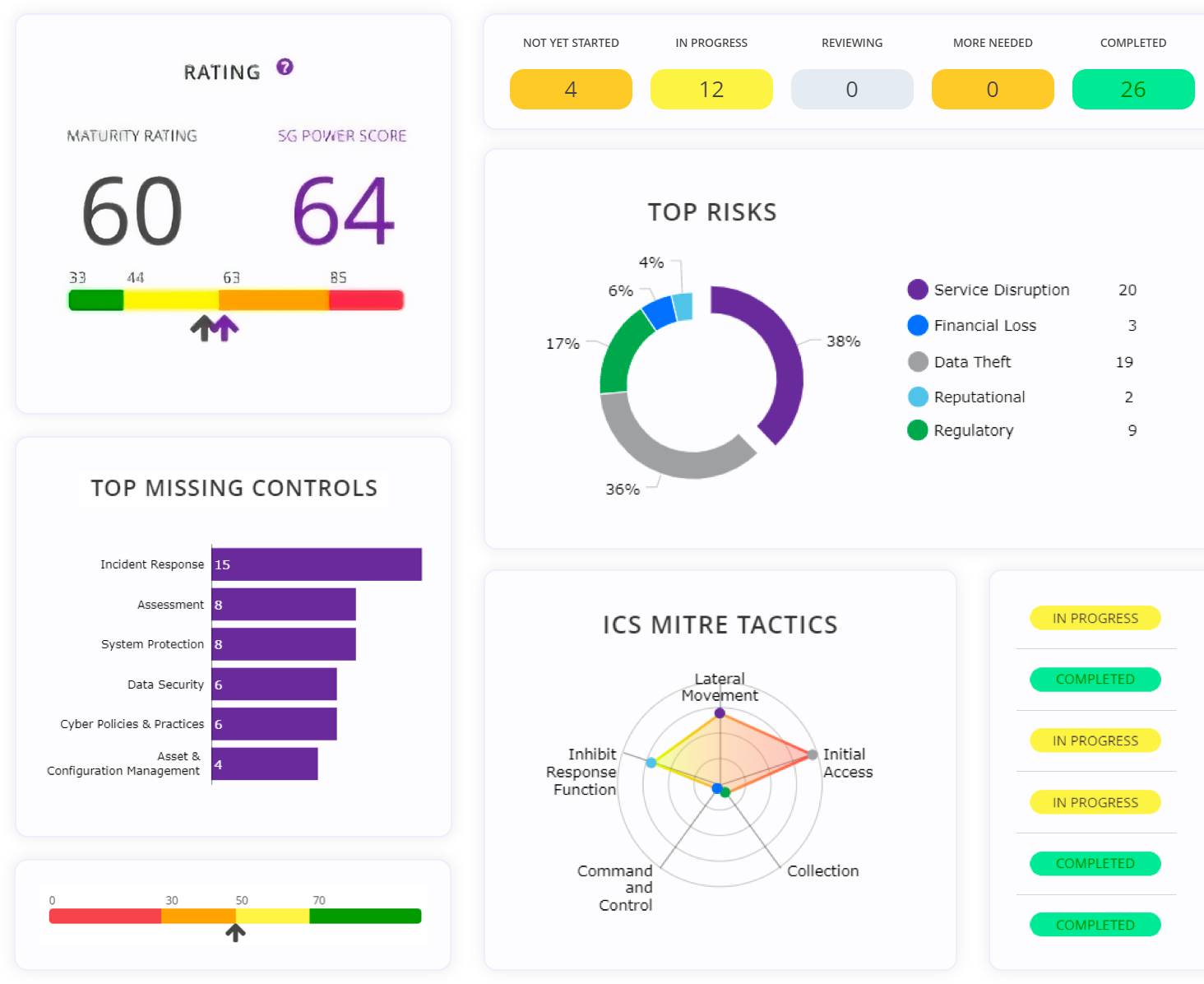
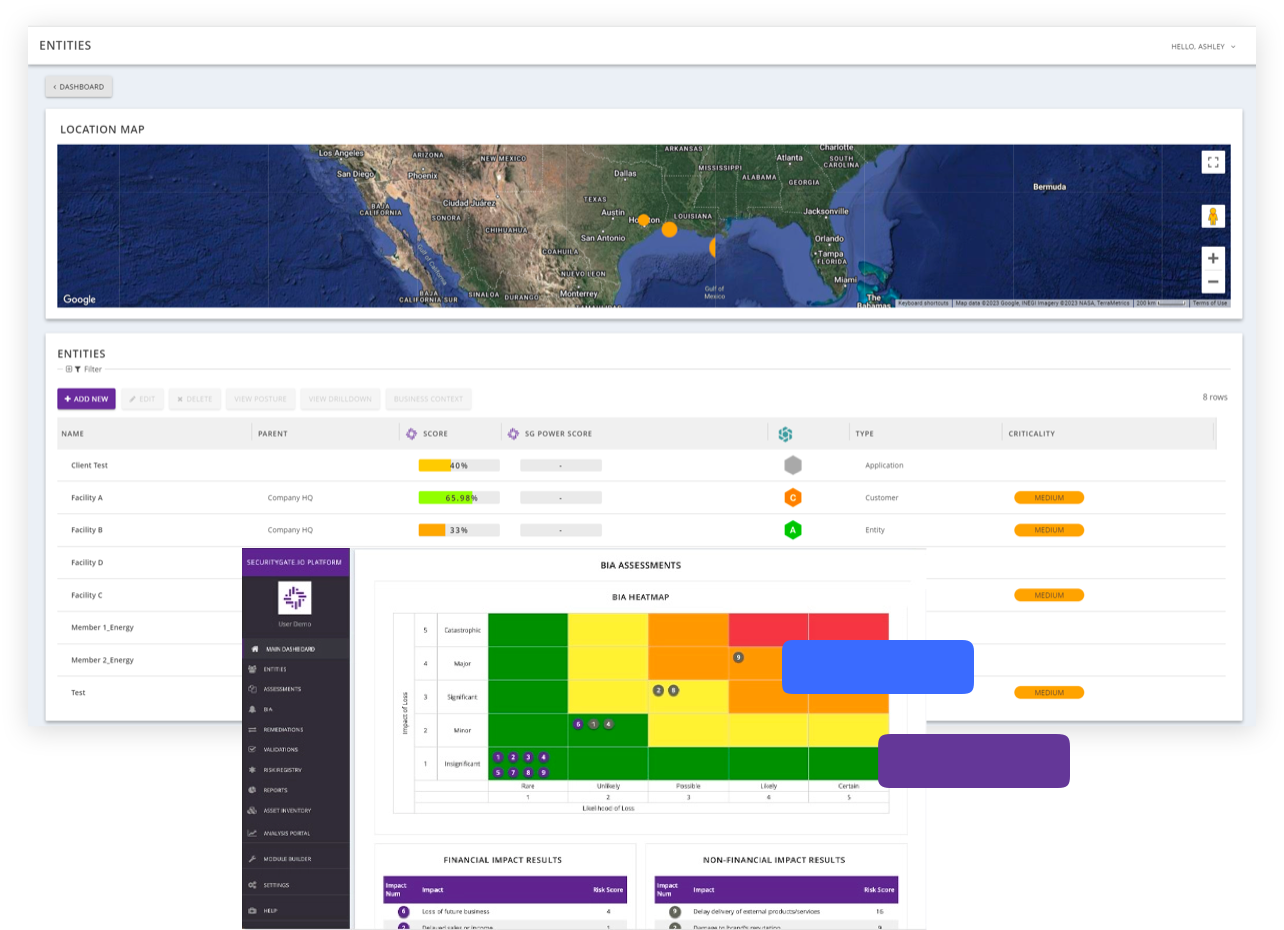
Communicate real-time metrics to senior leadership with a bird's eye view of your industrial ecosystem. Or dig into the details and view maturity or compliance by site, function, and geography.
Choose a Framework or Build Your Own
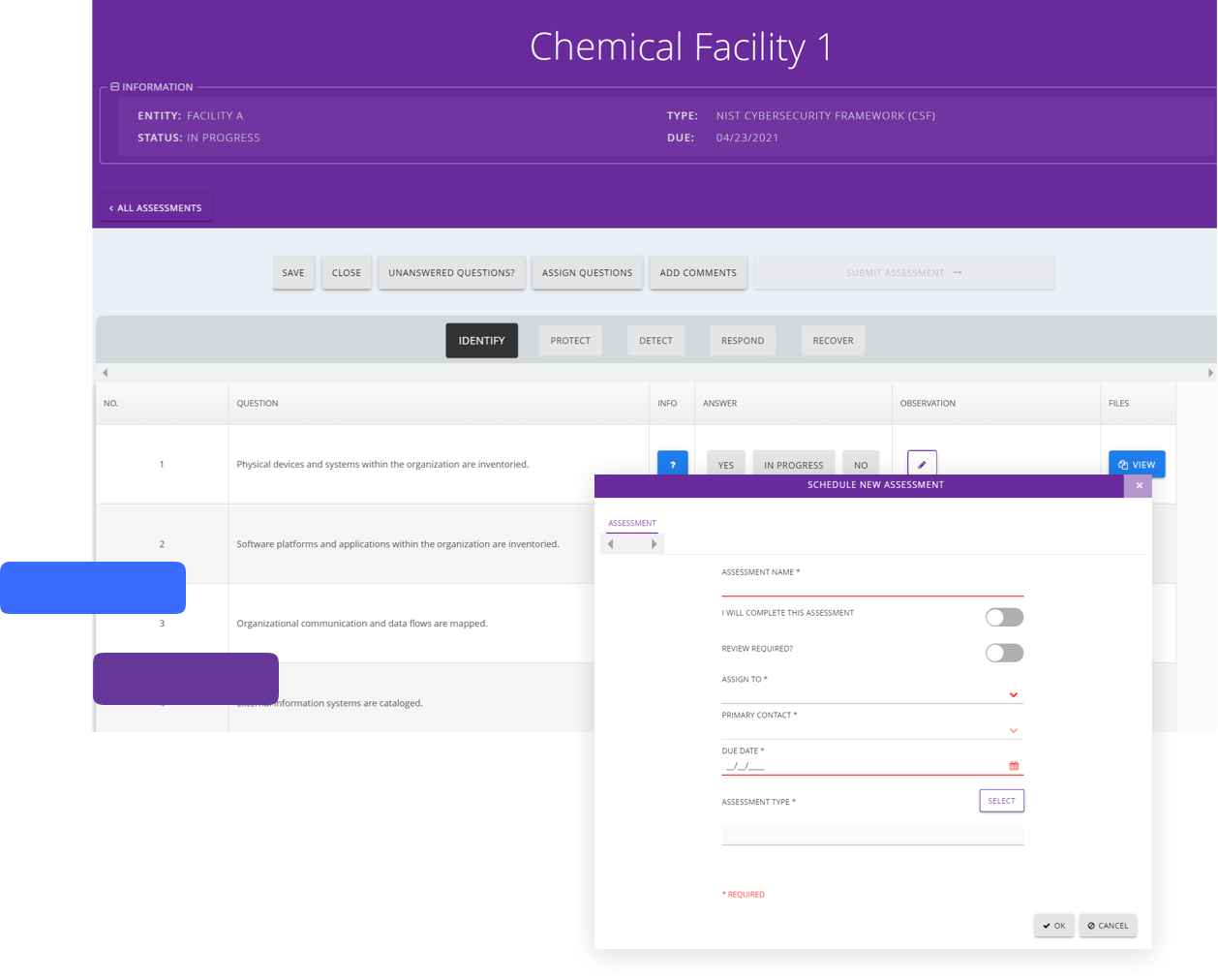
Quickly get started by choosing from over 20 industry frameworks (including NIST-CSF), uploading your own, or mix and matching over 3,000 control questions from our library to address your unique business needs.
Enable Collaboration Across Teams
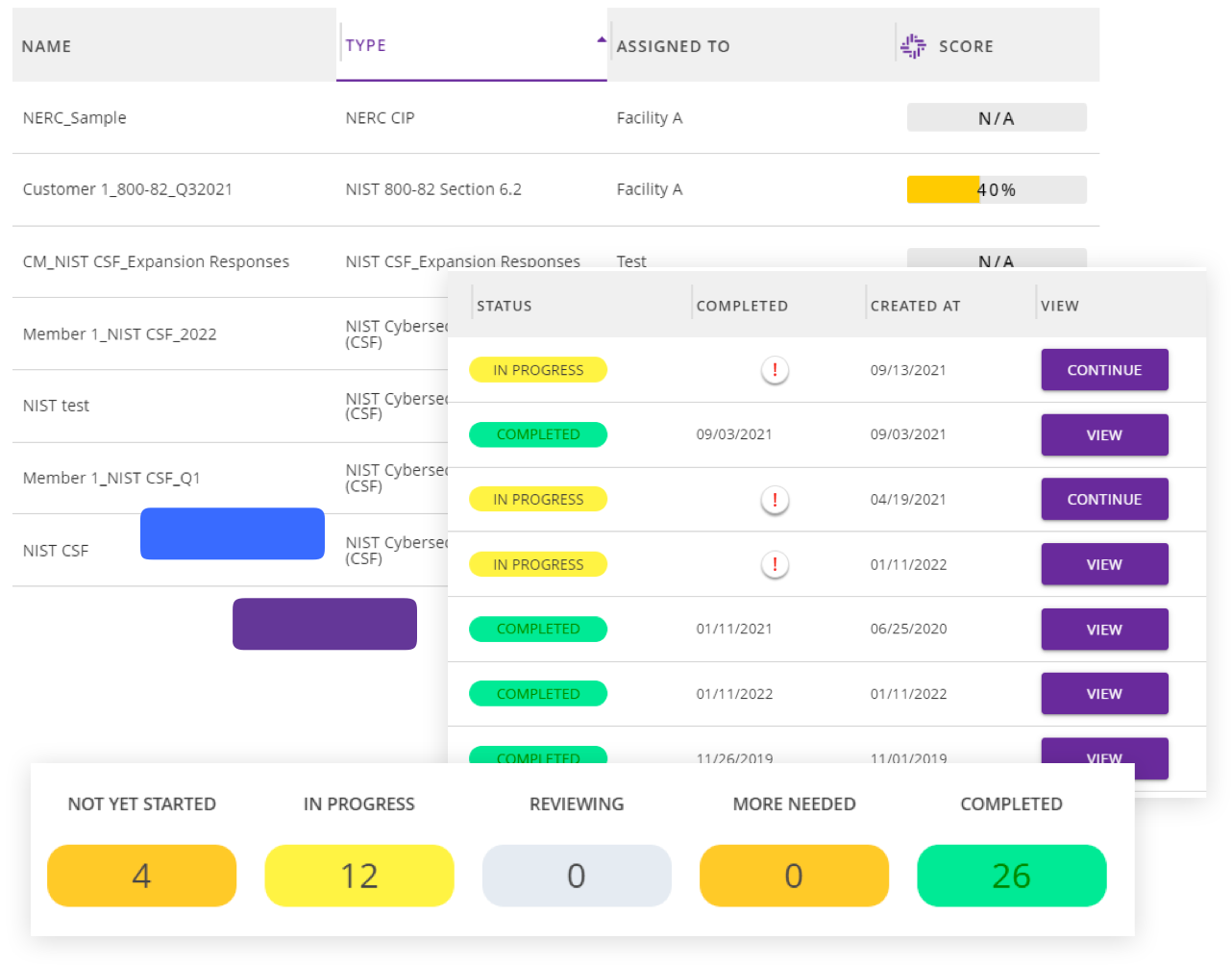
You're in command of data collection, review, and approval. Assign tasks to team members or third-party vendors and centrally manage feedback to quickly remediate issues.
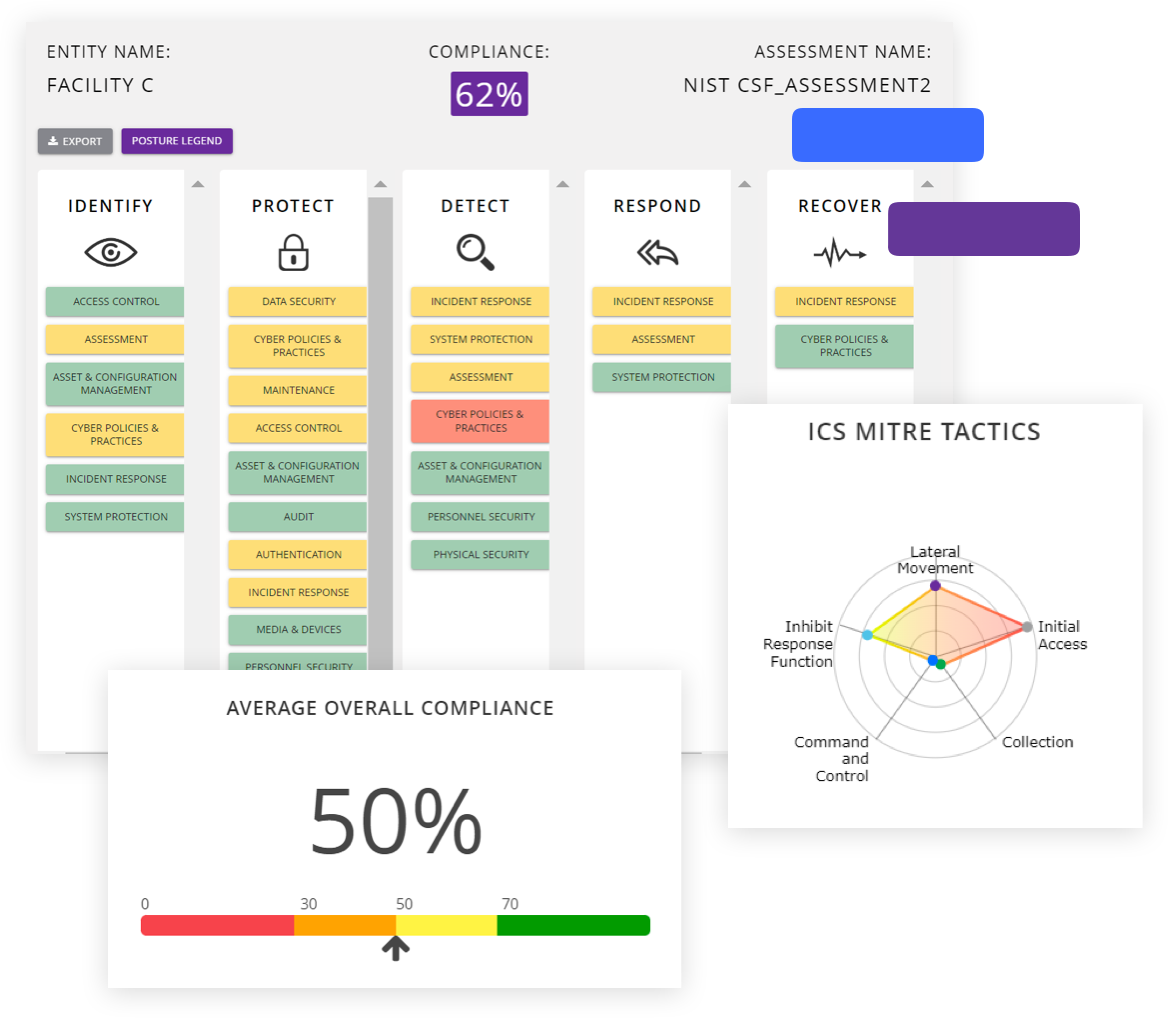
Drive Action with Visual Dashboards & Reports
Automated control mapping across threats, risks, control families, and impact levels will arm you with the insights you need to create an effective roadmap for improvement.
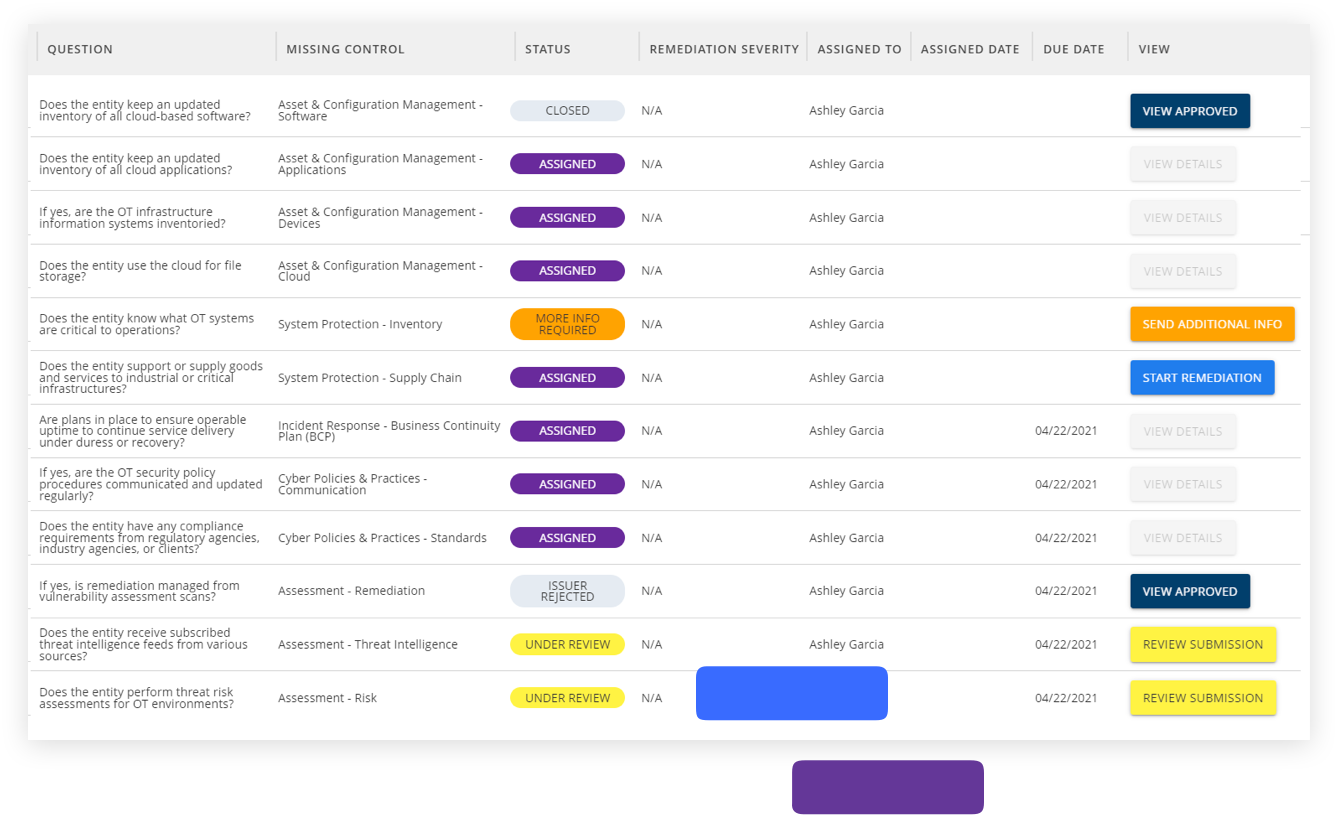
Manage Improvement at Scale
Assign and monitor remediations from within the SecurityGate Platform or tap into the open API to connect with your favorite ticketing solution.

Global Availability

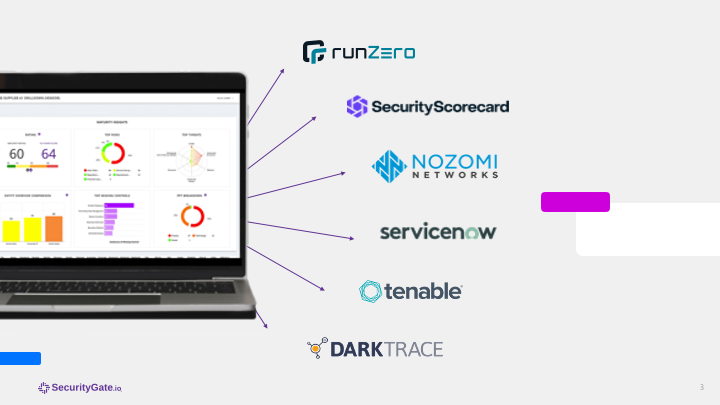
Native Integrations

Open API
Frequently Asked Questions
Our team constantly updates over 20 industry frameworks. Additionally, you’re free to upload and customize your own.
Yes, the platform can be used to perform assessments internally and externally.
Yes! Just upload into the platform, or use our question library to create your own.
We offer 2-Factor authentication via Google Authenticator, LastPass, and Microsoft Authenticator. Users also have the option to use BYOK inside their Amazon Web Service (AWS) environment.
We offer several native integrations with asset inventory tools and ticketing solutions. Check out our integrations page for more details. If you don’t find what you’re looking for, you can always use our open API to pull data into any tool you use.
Yes. Each assessment gives you the option to attach evidence or artifacts and document observations.