
CASE STUDY
Drilling Company Matures OT Cyber Risk Program with SecurityGate
About the Company
This SecurityGate.io customer is an oil-service industry leader, specializing in rigs and drilling equipment. For privacy and security reasons, they have chosen to remain anonymous for this case study.
Their Director of Security is in charge of ensuring all the industrial control systems (ICS) are secure and properly assessed for risks. With their operational technology (OT) networks being increasingly exposed to cyber threats, it was a challenge to figure out where they should start.
His lean department had a limited understanding of OT security, and it was unclear what responsibility the IT department had in cyber risk assessments. Additionally, they had no firm ICS asset inventory.
How They Matured Their Risk Management Program with SecurityGate
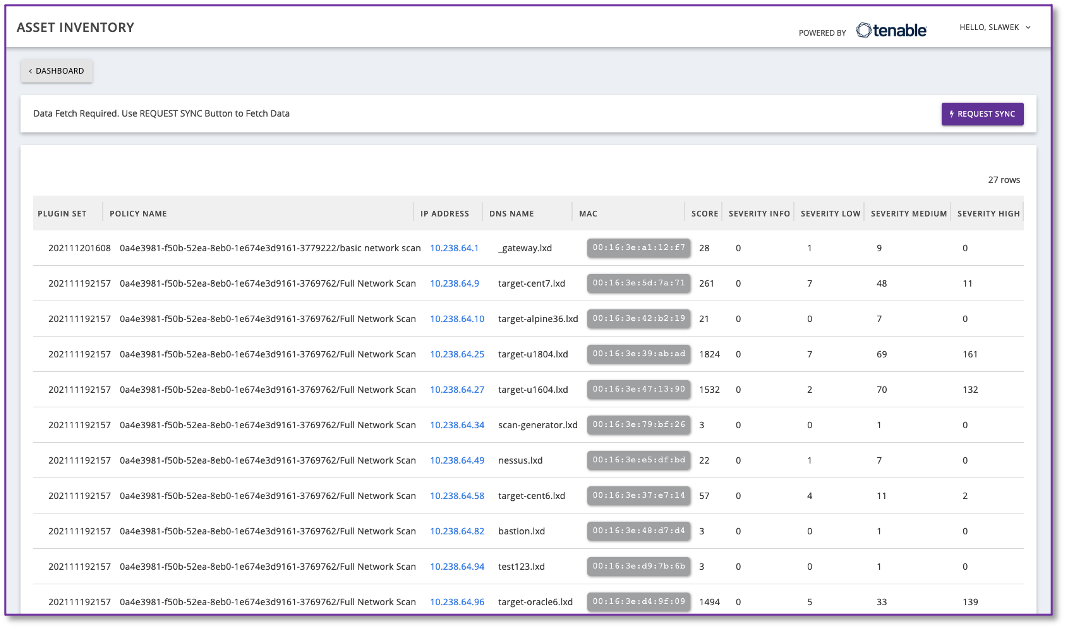
Complete an Asset Inventory
Without a clear understanding of what was on their OT network, this drilling company was vulnerable to cyberattacks. And once they completed an asset inventory, it was a complex task to translate the data into action items – one his team didn’t have the experience to do.
Using SecurityGate’s native integration with asset inventory tools, like Tenable, they were able to see how their CVE scores affected their overall risk posture.
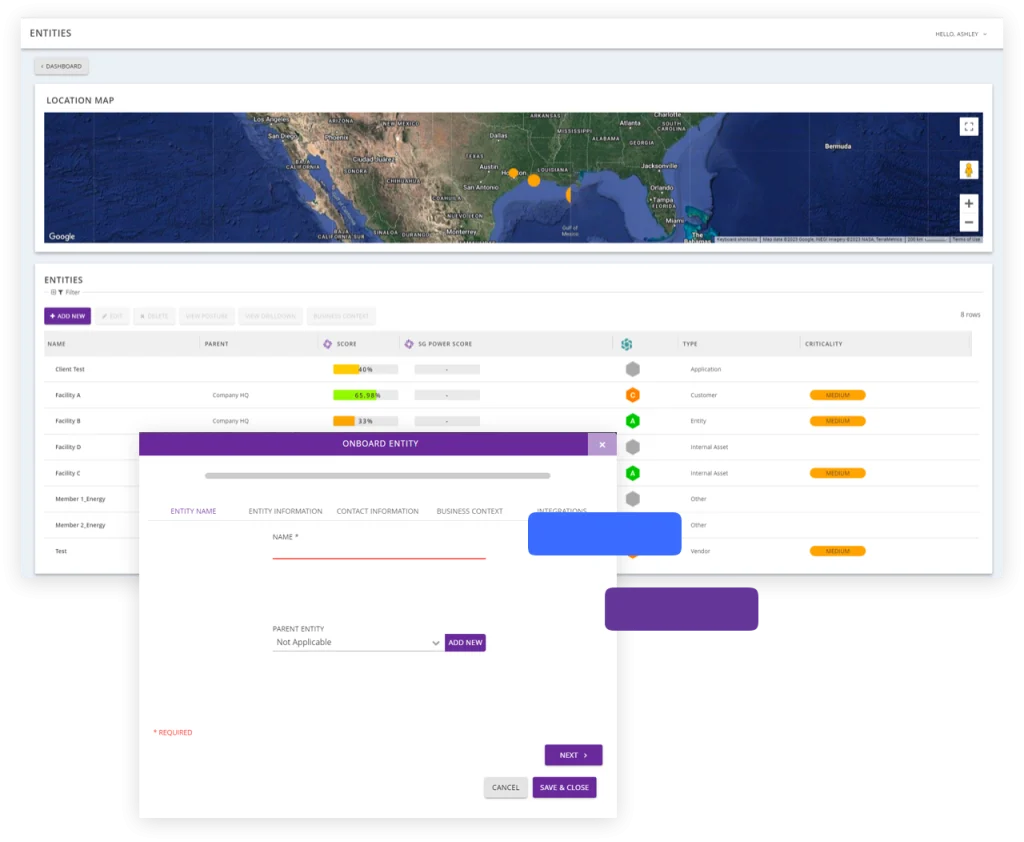
Establish Baseline Metrics
Before SecurityGate, the team relied on just two individuals to conduct risk assessments. This resulted in numerous challenges including a lack of consistency, employee burnout, and ultimately unreliable data. By using the automated workflows from the SecurityGate Platform, their team could perform assessments in record time. This enabled them to assess their global facilities and establish a starting point for maturing each one.
Prioritize Remediations with Reliable Data
Most importantly, the Director of Security now has a single source of truth for his executive team. The high-level reports and dashboards from the SecurityGate platform provide presentation-ready graphs to show the effectiveness of his program.
Decision makers have the insights they need tackle remediations and improve their security posture in a smart, cost-efficient way.

The Gift of an OT Cyber Security Maturity Playbook
For this company, the number-one feature of the SecurityGate Platform was guided assessments. The platform provided their inexperienced team with a predefined workflow and turnkey questions that addressed industry-specific risk scoring.
Not only did the automation from the platform save them a tremendous amount of time, they now have a repeatable process for next year’s assessments. Plus, the platform’s visual dashboards include a digestible view of how risk posture has changed for the company over time.







