In the wake of major events like the Kaseya ransomware attack, JBS meat plant hack, and T-Mobile data breach, 2021 was a big year for cybersecurity.
Governments around the world began enacting legislation to defend against cyber attacks. In the US, 35 states enacted bills centered around improving cybersecurity and the president issued an executive order to define how the federal government can assist. Australia updated its Security of Critical Infrastructure Act and the European Union passed the EU Cybersecurity Act to promote international cyber resilience.
The speed at which this dramatic shift happened was certainly warranted. Last year, 83% of critical infrastructure organizations experienced a breach. High-profile ransomware attacks also brought the importance of cybersecurity to the public eye not just via the media coverage, but the effects could be felt on a personal level. Hacks on digital infrastructure have consequences in the physical world. Thousands of people on the east coast could not access fuel during the Colonial Pipeline hack, and the Oldsmar community would have been devastated had the breach of their water supply plant not been stopped in time.
If 2020 forced us all to rapidly digitize our infrastructure, 2021 proved there is still a lot of work to be done to protect it. A top priority for many teams this year is to update their cybersecurity strategy to adapt to these new threats.
Bill Lawrence, currently serving as CISO at SecurityGate.io, has a wealth of experience directing risk assessment and mitigation activities within critical infrastructure across North America. As a trusted leader in cybersecurity, he continues to help organizations mature their security programs. Below he suggests three things organizations should consider as they rethink their strategy for 2022:
1. Focus on User Training & Technology to Prevent Successful Ransomware attacks
Ransomware attacks target organizations’ data or critical infrastructure, disrupting or halting operations. Often these attacks come in the form of an email which tricks their target into handing over sensitive information like usernames and passwords.
Lawrence urges the importance of holding regular training sessions for all employees that help them to identify illegitimate emails.
“Sharing what actual phishing emails and documents look like from the IT environment would help everyone know what to watch out for,” says Lawrence. “It’s much better than clicking the wrong link or file.”
Lawrence adds that there are also low-cost solutions that can help security teams manage the issue, though they are certainly not 100% effective. “Companies like Microsoft offer enhanced anti-spam and anti-ransomware protections, sometimes at just $2 or $5 per user per month. With the average cost of ransomware mitigation and/or ransoms hitting over $100k last year, that’s a lot of users you can protect while avoiding potential regulatory or reputational damage.”
2. Go Above and Beyond Compliance
Even though regulatory compliance and regulations have become more robust in light of major attacks, aiming for compliance alone is not enough to protect your organization. As Lawrence puts it, “compliance is a type of ‘you must be this tall to ride’ and a cost of doing business.”

Outline what areas would be most impacted if a few more dollars were strategically invested in them. Conducting a business impact analysis may help with identifying these areas.
“Going above and beyond in certain areas, like ransomware protection, disaster recovery/backups, and cyber security training will be well worth the investment. You may still get hit, so having appropriate levels of cyber insurance are a necessity as well,” Lawrence adds.
3. Invest in Your Subject Matter Experts (SMEs)
Organizations everywhere are struggling to find experienced cybersecurity professionals. If your team is lucky enough to have a SME on hand, you’ll want to ensure that this team member receives regular training to add to their toolbelt and give them opportunities to spread their knowledge to less experienced team members.
“Steady improvements in cyber PPT (people, process, technology) programs with thorough, regular risk assessments, can make you head and shoulders above industry peers who don’t invest in their PPT,” says Lawrence.
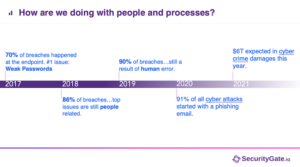

There isn’t one tool or set of tools that will prevent a breach. People are an organization’s most valuable asset when it comes to protecting cybersecurity assets. However, it’s also true that people are often the cause of breaches as well. By investing in your people and providing adequate training, your team will be able to identify attacks before they happen and be better prepared in case disaster strikes. “Train them like they’re never going to leave and they can expertly defend the crown jewels,” notes Lawrence.
Cybersecurity is a Team Sport
Teams that work in silos will find it hard to move the needle of maturity in the right direction. Whatever your cybersecurity strategy looks like in 2022, it’s critical that stakeholders are aligned on all the ins-and-outs. Be ready to communicate the “why” behind your recommendations with data. This information will also be useful in setting measurable goals or key performance indicators that indicate whether your strategy is effective.
Drive alignment within your organization by managing cyber maturity activities within the SecurityGate.io platform. Collaborate with facility owners and 3rd party vendors to quickly perform assessments and remediations. Plus you can easily monitor maturity progress from one pane of glass and share results with executives. If you’re interested in learning more about how SecurityGate.io can help your critical infrastructure organization, reach out anytime by chatting or booking a demo with our team.






